Gregory P. Bufithis, Esq.
Founder/CEO
The Project Counsel Group
14 September 2015 – Every summer I head home to Greece for a 2-3 week holiday to take a large chunk of time and “disengage” … fleeing my work-base in Paris. It is my time, where I read a bit, write a bit, sail a bit, and just plain veg. I follow the advice given to me long ago by Dominique Senequier (France’s private equity maven) who told me the trick to happiness and personal success is to be committed to all aspects of your life and disengage from the daily noise and make time for them: “Vous avez besoin de se désengager, échapper au bruit, se concentrer sur des thèmes et des tendances”. (“You need to disengage, escape the noise, focus on themes and trends”.)
This summer I packed 6 recent books that address the digitization of our lives, looking at it from the perspective of how I have lived through different stages of digital evolution. After three years on Wall Street (part of it as an M&A analyst for the media industry), I attended law school and established myself as an IP lawyer with digital media/digital technology as my specialty. When it comes to digital, we often focus on all things technology, but the need of the hour is to understand the changes wrought with respect to human conditions: the astounding changes in culture, language, political, and social development.
One brief example … digitization has created a new language that emerged with words, emoticons, abbreviations, etc. Slowly and steadily it crept into official communication. Most of us get emails with 🙂 and :-0 or ADAD, B4N, FUBAR, FYI, IDK, IMHO, etc. This language is open, fluid, ever-changing, and most importantly understood across the globe. Probably for the first time in modern history, a language has spread and been accepted without any form of pressure or imposition or destruction (killing people or burning books).
And in Israel … the ultra-Orthodox (or Haredi) rabbis found a “great spiritual danger”: WhatsApp. Turns out the app has become a popular method for their followers to form groups for exchanging gossip and even “immodest” images and video clips. So the rabbis issued a long list of edicts that included purchasing only specially programmed smartphones with filters keeping out all but rabbinically-approved data services. But many younger Haredim have ignored the edict, or instead buy two mobile devices: one for calls within the community, while tucked away in another pocket is a smartphone to keep up with the outside world. The path of righteousness is not easy.
I end the summer at DLD Tel Aviv. It’s Israel’s biggest tech conference but really much bigger than just a conference and properly referred to as an “Innovation Festival.” It’s where the Big Dogs like Facebook, Google, IBM, Intel, Microsoft … even Coke, Disney and LL Bean … unveil some of their “work-in-progress” funky tech. It’s technology you will eventually read about first in MIT Technology Review and arXiv Papers before it hits the mainstream tech media. And it’s a place to meet folks like Yossi Matias, the managing director of Google’s R&D Center in Israel and Senior Director of Google’s Search organization, and Aya Soffer, an IBM director behind Watson and IBM’s cognitive analytics programs.
Plus entrepreneurs and investors come from all over the world because the event features hundreds of startups, VCs, angel investors and leading multinationals looking for the latest tech.
And there is very much the feeling of an “unconference” (much in vogue these days) because it is loosely structured. Yes, there is a program but there is an emphasis on the informal exchange of information and ideas between participants. I attend ten technology-related conferences a year and this one clearly is the most energizing with the most freewheeling exchange of information and ideas.
Fun disclosure: following the lead of Dylan Matthews at Vox I decided to sign-up and have a chip embedded in my hand, a glass-encased RFID/NFC chip. If you scan it using an NFC reader/writer (included in many Android phones, and the new iPhone 6 series) you can store information in it, and read the content off your phone. And if you have an iPhone you can use it in lieu of a PIN or pattern to unlock your phone, or if your office requires key fobs, you can register the identifying information in the chip with your building staff and just wave your hand at the door or in the elevator, saving you the trouble of pulling out your fob. Oh, and all kinds of other cool stuff. More to come in a subsequent post after the implant.
I was only able to attend three days of the week long event (some amazing sandstorms included at no charge) but I collected gigabytes of information that will provide content for future posts. Herein just a few notes I’d like to share:
IBM Trumps “The Donald”
IBM’s shift from hardware to business intelligence and data analytics has been much in the press, especially Watson. We have seen Watson in healthcare, finance, government, retail and even in writing recipes. Over the last several years I have had numerous meetings with IBM Watson staff and their cognitive computing teams, and this past June their cyber security team. I have also been through one of the IBM Watson Ecosystem programs.
FULL DISCLOSURE: IBM was my first IP client when I started my legal career on Wall Street. I have stayed in touch with scores of IBM-ers throughout my career.
Its use has not been lost on the legal industry. For an excellent analysis of Watson in the legal profession I recommend Ron Friedmann’s series (click here).
I am more familiar with its use by the Memorial Sloan Kettering Center and cancer treatment having attended the various exponential medicine summits. The center’s clinicians and analysts have been “training” Watson to extract and interpret physician notes, lab results, and clinical research, teaching Watson how to translate data into actionable clinical practice based on a patient’s unique cancer. Cancer is not one disease but a cluster of diseases with hundreds of subtypes, each with a different genetic fingerprint. Although significant discoveries have delivered extraordinary insights into cancer biology and strategies for targeting specific molecular alterations in tumors, these advances have also increased the complexity of treating individual patients. Vast amounts of rapidly changing information means it can take years for the latest developments in oncology to become standard care across all communities.
When utilizing Memorial Sloan Kettering’s breadth and depth of experience, gained from treating more than 30,000 patients with cancer every year, Watson takes information about a specific patient and matches it to a huge knowledge base incorporating published literature and the treatment history of similar patients. Watson’s ability to mine massive quantities of data means that it can also keep up – at record speeds – with the latest medical breakthroughs reported in scientific journals and medical meetings. Additionally, because it utilizes cognitive computing, Watson continually “learns,” thereby improving its accuracy and confidence in the treatment options it suggests.
IBM found inspiration to take cognitive computing further after Deep Blue became an artificially intelligent (not “artificial intelligence”) chess-playing champion. In 2011, millions of viewers watched IBM’s Watson beat the top 2 reigning champions of Jeopardy!; however, viewers actually watched an avatar on the game show as the massive Watson sat in another room of the building. Roughly the size of 10 refrigerators, this supercomputer boasts 90 servers and 15 terabytes of RAM. This Jeopardy! win constitutes the extent of most peoples’ knowledge of Watson, but, behind the scenes, the expertise and information required to develop Watson’s architecture challenged IBM on a whole new level.To answer a question, Watson first decomposes it to pull out the relevant fact(s), then searches through its vast stores of data (and the internet, if applicable) for content related to them. This content is analyzed to formulate any number of hypotheses for further evaluation. The hypotheses then go through further analysis to find evidence to support or refute the hypotheses. Finally, Watson uses a combination of its 50 scoring components to assign scores to each hypothesis with a higher score indicating more confidence in the answer. This iterative process ensures that Watson is constantly learning. In 2008, this process took Watson 2 hours to answer a single question. Now, the supercomputer can answer a question in approximately 3 seconds.
One thing is certain: CEO Ginni Rometty is betting big on Watson. When she made a presentation at the Mobile World Congress last year (an event I attend every year) she spoke of IBM’s $1 billion in guaranteed funding going into the project over the next several years – with a large chunk being offset to the new free Watson Analytics platform. She is making a real long term commitment to the technology.
Financial analysts say that all of this is fine. Watson is no doubt a formidable hammer, but it needs to find enough nails to prove its worth. IBM does tend to put a happy face on the capability of Watson with press release after press release of “collaborations” and “associations”. For the analysts, they want to see some mega-$-deals and “systems in action” and hard data, and not PR fluff about functionality to show this shift is viable.
So … finally … something really important: analyzing the personality of Donald Trump!
IBM’s Watson is being employed in a new and interesting way: your writing. IBM Watson Personality Insights will tell you what your writings say about you. The software derives cognitive and social characteristics about people from their writings, using linguistic analytics. I never thought I’d see a direct comparison between speeches of Donald Trump and Abe Lincoln (Lincoln’s Gettysburg address was used as a control), but there you have it. There are actually some similarities; they’re both businessmen turned politicians, after all.
Watson’s take on Trump’s “We Need Brain” speech from the Republican primary debate last month:
“You are a bit dependent, somewhat verbose and boisterous. You are susceptible to stress: you are easily overwhelmed in stressful situations. You are emotionally aware: you are aware of your feelings and how to express them. And you are prone to worry: you tend to worry about things that might happen. Your choices are driven by a desire for efficiency. You consider both independence and helping others to guide a large part of what you do. You like to set your own goals to decide how to best achieve them. And you think it is important to take care of the people around you.”
For comparison, the write-up for the analysis of Lincoln’s Gettysburg Address (rest assured, Lincoln does come out looking better than Trump):
“You are genial, expressive and confident. You are confident: you are hard to embarrass and are self-confident most of the time. You are self-controlled: you have control over your desires, which are not particularly intense. And you are empathetic: you feel what others feel and are compassionate towards them. Your choices are driven by a desire for connectedness. You consider both independence and helping others to guide a large part of what you do. You like to set your own goals to decide how to best achieve them. And you think it is important to take care of the people around you.”
You can do your own analysis. You submit between 3500 and 6000 words for Watson’s psychoanalysis penned by yourself, a friend … or an enemy (click here).
To investigate the software’s methodology, click here.
Side note: IBM had the nerve to unveil its the brain-inspired TrueNorth cognitive computer while I was on vacation. I managed to pop out a brief post (click here).
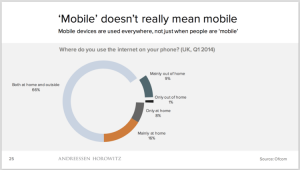
Is the “mobile internet” just “the internet”?
This is not a new question but it was discussed quite a bit in relationship to new mobile apps and use of the internet in general. For as long as the idea of the “mobile internet” has been around, we’ve thought of it as a cut-down subset of the “real” Internet. Many think we need to invert that – to think about mobile as the real internet and the desktop as the limited, cut-down version. Once, they say, it made sense to think of mobile as a subset of the internet. Phones themselves could only do a little bit of the internet. It was partly as a result of these limitations that our mental model of how and where you used “mobile” was that it fitted into specific, occasional places and times where you were walking or waiting or needed a single piece of information and didn’t have a PC.
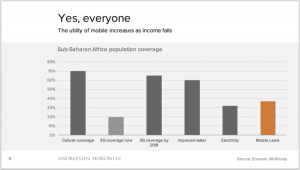
And it has gained a lot of traction as the result of two graphics produced by Benedict Evans of Andreessen and Horowitz:
This is not just about people in rich countries. Of 5bn adults on earth today, close to 4bn and growing have a mobile phone today, almost all of whom will convert to smartphones over the next few years. The entry price for Android has already fallen to under $40. There’ll be lots of grey areas in this – what people pay for connectivity, and to charge their phone – but mobile is a universal product in a way that the PC never was. Indeed, the lower your income, the more valuable communications becomes.
Side note: when you watch the news videos of the Syrian and other refugees arriving by boat and dinghy on the Greek island of Kos (just off the Turkish coast), and the Malta and Italian coastlines, note all the mobile phones they carry.
So, the argument is that mobile today does not mean “when you’re mobile”. It means ubiquity – universal access to the internet for anyone at any time. People use their smartphones all the time, very often when there’s a PC in the same building as them or the same room, or on the sofa next to them.
I am of a different camp. I actually think that there are two different Internets: one is for work and is tied to the larger screen because, let’s face it, no one will do complex spreadsheet analysis on a small screen. People won’t compose documents easily on an iPad or a iPhone 6+. Try as I might … and my colleagues at IBM did a very nifty job last year jail breaking it and modifying it with holographic displays and a virtual keyboard and nifty software … I could not make my iPad my sole devise. I needed my laptop.
There is a “real-estate intensive” Internet, where, actually the quality of interaction may be much higher. And there is the mobile Internet, which takes up a greater chunk of time and is a more preferred content consumption platform for everything from long-reads to shopping to skip-turn-skip. And if you are a sailor it is incredibly helpful.
But they will be very divergent uses with divergent paths. And if the McKinsey and IDC studies are correct, even as mobile grows, it’s not necessarily stealing time from larger screen computing. What it is doing is stealing time from TV, radio, and other mediums.
Marshall McLuhan was right: “the medium is the message”. How these devices are changing our lives.
▪ Technology, intellectual property and e-discovery
I manage a fair amount of e-discovery work across Europe as the Managing Director of eTERA Europe, much of it in the area of technology-based intellectual property disputes. I find that attending events such as DLD Tel Aviv and the Mobile World Congress informs my work because it is key to understand the technology at issue. It makes you much more effective in e-discovery matters. Sometimes I think as lawyers we love to use the products of technology but are not keen on learning the science.
Take the most extreme situation. Last week the U.S. was forced to drops charges that a professor had shared restricted technology with China. The gist? The schematics in possession of the professor, the prosecutors said, revealed the design of a device known as a pocket heater, a restricted devise. Except that … well, the blueprints were not for a pocket heater. And that was only discovered 6 months into the case at great expense and loss of reputation to the professor. It seems nobody in the U.S. Attorney’s office did their tech homework.
Today’s technology products are so complicated that one firm cannot build the entire product anymore. Many important breakthroughs have their roots in theoretical research that is rarely built by their inventors. Take the wireless cellular network as an example. Each new generation of the wireless network utilizes some fundamental academic idea invented more than ten years before as its main driving force, developed and improved by multiple parties. The network is built by so many companies spending millions of dollars to develop those ideas as products years later.
Technology is complex and requires some deep understanding. DLD is one of those places where you’ll find a tech expert in almost every field.
And there is always a bevy of IP lawyers and cyber security lawyers at DLD. Plus this year we had two e-discovery lawyers. Wow.
A few items of conversation with the lawyer pack:
– Recently this has been a well-documented trend discussed in many legal blogs. Hackers have been targeting businesses’ advisers, most notably law firms. According to a representative from the FireEye investigative response division, professional services firms are the third most targeted type of organisation.
– The black market is thriving. For companies, buying information from a hacker poses far fewer risks than paying someone to steal physical blueprints or files. Lawyers in industries such as pharmaceuticals and technology as well as defense have seen products emerge that seem to draw heavily on their stolen intellectual property.
– Intellectual property litigation is one of the more complex and costly types of litigation that businesses encounter. Many companies see copied versions of technology they have patented, in many cases capitalizing on their company’s pioneering efforts. But rather than pursue patent violations through expensive lawyers, they focus their efforts on engineering developments and improvements. In that way they hope to keep ahead of the competition by consistently providing a better product.
– And a nod to information governance. In intellectual property litigation, where records can carry information concerning the proprietary process or trade secrets of an organization, the risk of data breach is compounded by the potential release of privileged information to legal opponents. The probability of a competitor using leaked documents to gain a market advantage is relatively low and would likely result in additional litigation not to mention criminal action. The legal fallout heralded by the use of intellectual property erroneously or maliciously collected by competitors is generally enough to dissuade foul play in the discovery process.
However, in a data ecosystem that has grown dramatically over the last few years, the prospect of losing critical documents that contain such information is not impossible. Said one of the in-house e-discovery lawyers at DLD: “Look, I am not a fan of what is being sold as “information governance” at events like LegalTech and ILTA. Just the newest fad to sell as vendors go through their marketing contortions. Yet another product to flog like early case assessment and predictive coding. Few of these vendors and so-called IG experts know what they are talking about and they will fold if you drill them deep. BUT … when it comes to proprietary information I agree you need a damn strong information governance policy in place. But it ain’t coming out of a vendor’s box. You need to think it through and build it.”
His company first assembled an IP protection team with personnel from all relevant departments. They then built IT security systems and an array of tools including encryption of confidential information, plus a system whereby electronic documents are created so that some only exist for a limited amount of time, some can only be accessed with a special code, and all are restricted from being saved, forwarded, or printed. For conducting electronic discovery on this stored information they constructed virtual infrastructures and displays with the aid of an enterprise search vendor with e-discovery capability (named, but I may not disclose).
▪ Some funky tech I am eager to see
I cannot possibly recap all the innovative tech I saw. But one development really intrigued me.
The touchscreens on computers, mobile phones and other digital devices are printed with a grid of transparent conductors. When nothing is nearby, the electrostatic field created between the conductors is smooth and even. When a conductive object, like your finger, is brought very close (touching or within a few millimetres) the field becomes disturbed, which shows up as a small change in the capacitance (a measure of the ability to store a charge) between specific conductors in the grid. This provides the co-ordinates of the finger immediately above or on the screen. It is also possible to detect some gestures, like “pinch and zoom”, but only if the fingers are on the surface of the display. Your finger, a pointing device such as a mouse, or a specialist controller are required.Google’s Project Soli, Fogale Sensation (a startup in Geneva, Switzerland), and Apple (among others) want to change that. They are developing ways to use hand and finger gestures to produce true 3D interaction with computers and other digital devices. The goal is to produce a successor to the mouse — which is prehistoric in computer terms, having emerged in the 1960s.
What they are doing is developing an array of sensitive transparent sensors, each microscopically connected to the ends of the screen. These effectively “triangulate” the location of a finger or hand above the screen by measuring the change in capacitance between nearby sensors. A number of techniques are used to eliminate false signals and “noise” caused by the hotbed of hardworking electronics below the screen. Smartphone screens have been growing steadily larger, but this has been at the expense of becoming increasingly difficult to use with only one hand. Side-touch sensing would detect when a user is stretching their thumb across the screen, and bring the on-screen button they are trying to reach closer.
And, an added security feature. The screen could also track gestures, opening up the possibility of unlocking a phone with a complex hand movement accompanied by speaking a security word: “shalom”, for instance.
And the magic could go further. Google sees possibilities in other areas, such as allowing people to use their fingers and hands in more natural and intuitive ways to assemble, shape and manipulate virtual objects in computer systems. Making such software even easier to use would no doubt improve the handiwork of those creating things in what developers call “the third dimension”.
The Congress is the brainchild of Frederick Gyebi-Ababio, Director of INsig2 LawTech Europe Congress. Its mission is to create a cutting edge forum that addresses four core areas; digital evidence, forensic investigations, data analytics, and legal efficiencies. Fred has done a remarkable job of achieving that mission.
The event is becoming a “must attend” for the e-discovery community in Europe. Attendees will be engaged throughout with advanced topic presentations, panel discussions, and an array of latest solutions from credible exhibitors.
They keynote addresses are by two of the brightest stars in the legal firmament:
Ralph Losey, predictive coding pioneer, whose address is titled “The Future of the Law: the impact of artificial intelligence and other advanced technologies on the search for truth and justice”, and
Markus Hartung, director of the Bucerius Center on the Legal Profession at Bucerius Law School, Hamburg, whose keynote will focus on “Technology and trends in the legal market: disruption, evolution or – just hype? Perspectives from the European market”.
For full details on the program, the speakers, etc. go to: http://www.lawtecheuropecongress.com