[ pour lire cet article en français, cliquez ici ]
[ per leggere questo articolo in Italiano clicca qui ]
31 July 2019 (Chania, Crete) — As I have noted before, the content (and conversations) available at an event like the International Cybersecurity Forum in Lille, France (“Le FIC”) can be enormous. When you have the brain power in attendance at an event like Le FIC, you cannot help but have deep conversations on all aspects of technology, and not just cyber … subjects you tend not to address at other conferences like the complexity of computer systems, the multi-sided/holistic approaches to take to technology issues, etc.
So you need to grab these brilliant people, these fabulous knowledge channels … folks like Michael Daniel (CEO, Cyber Threat Alliance); John Frank (Vice President, European Union Government Affairs, Microsoft); David Grout (CTO for EMEA, FireEye); Alexander Klimburg (author, The Darkening Web); Pascal Le Digol (Country Manager, France, WatchGuard); Philippe Dubuc (Cyber Solution Architect, Ping Identity); Colonel Cyril Piat (Deputy Head, Digital Crime Combat Division, France’s Ministry of the Interior) … to name but a few.
And then couple that with intense 1-day and 2-day cyber security workshops throughout the year sponsored by individual vendors like Fireye and your education is complete.
Which takes me to one of those specific cyber security mavens I noted in my opening above, David Grout of FireEye.
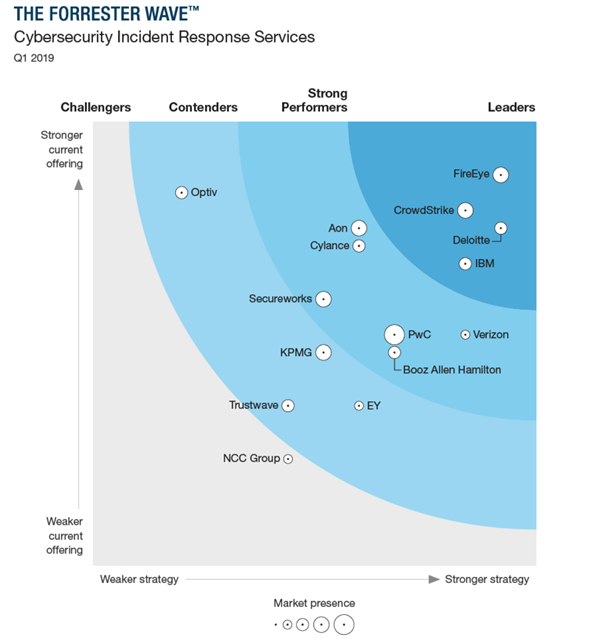
FireEye is one of the leading world-wide cybersecurity companies providing hardware, software, and services to investigate cybersecurity attacks, protect against malicious software, and analyze IT security risks. And in fact it is the leader in cyber security incident response services.
I have known David for several years and he is simply a fount of knowledge on artificial intelligence, nation state hacking groups, critical infrastructure and utilities being targeted by cyber attacks, financially motivated cybercrime … oh, the list goes on and on. He is one of the most “in demand” speakers at Le FIC, and countless other cyber security events. It was David who introduced me to the concept of a “supra threat actor” which describes threat actors that represent multiple countries, institutions or groups.
I also stay up-to-date via “M-Trends” (based on FireEye Mandiant frontline investigations, reports on high-interest, significant cyber attacks across multiple industries and regions) and “The Vision” (a broader look at security issues across the entire cyber landscape).
It was also through David I was able to fine tune my understanding of the different skill sets necessary to address cyber-enabled information warfare (my area of interest and expertise) as distinct from cyber warfare; the former targets human minds, whereas the latter targets computer and communications systems.
Now, on to the Italy event.
A taste of the FireEye Milan, Italy event – an excellent way to learn how FireEye cyber security solutions can protect your organization against malware, zero days, and other cyber attacks.
The possibility of targeted cyber attacks, sponsored by foreign states, against Italian production facilities is not a science fiction hypothesis, but rather a concrete one. Although it probably concerns mainly those companies that have installations in areas geopolitically at risk, according to David.
He was in Milan last month to speak at an event where FireEye brought together all of its Italian partners. On this occasion, FireEye officially announced the acquisition of Verodin, a company operating in the Security Instrumentation segment. Verodin’s platform adds significant functionality to FireEye’s product portfolio by identifying critical points in a security environment due to configuration errors in IT systems, changes in the environments themselves, evolution of attackers’ tactics and more.
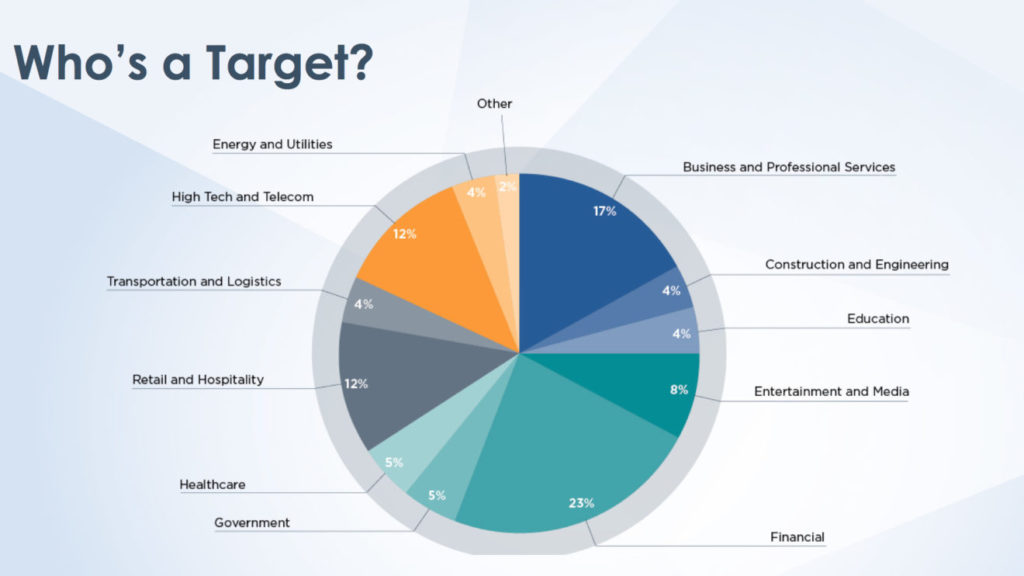
Which sectors are most affected by cyber attacks? According to FireEye, it is mainly the financial sector that is being targeted, but attacks against other players, such as government agencies, are increasing. David provided a slide to give an overall view:
Attacks on the production domain
David helped the attendees understand what is concrete in the information, often alarmistic, on the risks for the OT (operational technologies, the domain of production) deriving not from simple cyber criminals, but from organizations connected in some way with foreign governments, which would be active in both cyber espionage and cyber sabotage.
- In his presentation, he made a clear distinction between cyber criminals, who are essentially dedicated to attacking practices that allow them to earn money quickly – from extortion with ransomware to the theft of bank credentials – and other types of attackers with more “political” motivations.
- On the one hand, cyber activists, or groups that attack political opponents or companies identified as “bad” – for example, because of a lack of ecological awareness, or because they are engaged in delicate areas such as studies on GMOs; on the other hand, groups of cyber espionage, very often linked to government entities, dedicated mainly to the theft of industrial secrets, process technologies, and in general, intellectual property.
Among the preferred prey of these groups we find, recently, also information on the methods of certification of products to achieve compliance with European and American regulations. But can these groups represent a risk for the security of the TM in a country like ours, where cybersecurity in the factory is still a novelty?
One of the journalists present at the event approached David with four questions:
- We normally associate government-sponsored cyber attacks with problematic geopolitical areas such as the Persian Gulf or Ukraine. But, realistically, what is the level of risk for the Italian OT (operational technology)? What is, for the manufacturing companies, the probability of being attacked in a scenario of cybernetic war?
I see two main risks for the Italian OT. First, there is the fact that Italian companies are deployed throughout the world and especially in the Middle East for the energy sector and could be targeted by attacks by hostile governments because they are part of local geopolitics. The second aspect concerns pandemic or opportunistic attacks: the Italian IT market, like other European IT markets, is exposed to opportunistic and pandemic risks between OT and IT, the “notpetya” attack was an example in 2017.
- Cybercrime or cyber-activists: who represents the most dangerous threat to Italian companies, particularly from an OT point of view?
Both are worrying. As far as cybercrime is concerned, customers in the energy sector are interesting targets for attackers, they could be targeted by spear-phishing, extortion and other types of attacks. Also from the point of view of IT activism, the OT sector is exposed, but probably less so than IT today.
- It has been said that any international agreement, treaty or initiative generally triggers a reaction in terms of IT activity. Has Italy’s recent pact with China on its participation in the so-called “Silk Road” project produced any kind of state-sponsored attack on Italian structures? Is it possible that it will do so in the near future?
Currently NATO has recognized the contents of the Tallin 2.0 project as rules of engagement in case of cyber-attack. However, cyberspace is still not really regulated (the Tallin 2.0 manual does not have a formal legal value). State-related groups operating from China are quite active around the Belt and Road (BRI) initiative, called Via Della Seta in Italy. It is always difficult to predict the future, but we can certainly predict an increase in cyber attacks from groups such as APT40 in Italy.
- With the industry revolution 4.0, the use of commercial smartphones and tablets for remote control of production facilities is growing. Are we underestimating the risks posed by intrinsically insecure portable operating systems? Can attackers infect these devices to enter production facilities and from there attack not only the OT, but spread into IT?
The challenge in the industry is always the same: increasing the attack surface by introducing new devices is a risk, but companies must continue to innovate. To limit the potential risks, it is important that the industry anticipates attackers’ strategies through intelligence and understands the attackers’ techniques, tools and procedures. At the same time, you need to be able to evaluate, measure and adapt your information security structure. This is a key factor in making the adoption of 4.0 industry a success.
Other points and speakers at the Milan event
Companies are learning to respond much faster to cyber threats, but attackers are using increasingly sophisticated attack techniques and continue to multiply day by day. Italy itself is now a land of numerous groups of attackers, activists ready to launch offensives against government sites and corporate portals not only national. Marco Riboli, Senior Vice President Southern Europe of FireEye, said:
The message is clear: today no company, whatever its sector, can consider itself safe. This is demonstrated by the findings of our latest M-Trends 2019, the report in which we collect the global data of all investigations conducted by Mandiant during 2018. There are, of course, markets more besieged than others, such as Finance, professional and business services, Retail & Hospitality and Telco.
Marco Riboli, Senior Vice President Southern Europe of FireEye noted:
A worrying scenario, in which it is certainly positive to observe the general improvement in response times to violations suffered by companies. It’s worth remembering, however, that attackers only need two days’ stay in an IT infrastructure to cause unimaginable damage. According to our Mandiant surveys, in 2017 an average of 58.5 days passed worldwide between the start of an intrusion and its detection. In 2018 this number dropped to 51.
David had the opportunity to jump back in and he said:
This is an important step forward, which unfortunately still sees the Emea back, standing at 61. Also worrying is the figure for targeted compromises. Those who have been victims in the past are likely to be victims in the future. This is confirmed once again by our data in M-Trends 2019, according to which 64% of all customers managed by FireEye for detection and response activities were again targeted in 2018 by the same group of attackers or by one with similar motivations. This figure is up sharply from the 56% recorded in 2017.
In general, in Italy there are three types of attacks that are most common:
1. cyber espionage
2. cybercrime and
3. activism
According to David:
In our findings, the first and third have a fairly moderate level of risk. Cybercrime, which is the most recurrent type of attack and therefore has a much higher level of risk, is of more concern. Fraud, theft of personal and business data, and the use of ransomware fall under this category. But you must look at the spread of mobile devices which pushes the widespread use of mobile malware as an effective method of compromise.
A new piece in the assessment of security controls
FireEye responds to a scenario of increasingly diversified and evolved cyber threats with a virtuous cycle of innovation, based on three main components:
1. a strong intelligence capacity that allows it to know threats and attackers, thus strengthening protection and reaction;
2. a platform including tools for detection, investigation, automation and remediation; and
3. a solid ability to Incident Response.
This all-round proposal recently saw the addition of a new element with the acquisition of Verodin and its Security Instrumentation platform for the evaluation of security controls. In essence (as I understand it from the presentation and reading the fact sheets) what Verodin’s solution adds to the FireEye product portfolio are new and significant features to identify gaps in the effectiveness of security environments, shortcomings due to configuration errors of It systems, changes in the environments themselves, evolutions in attackers’ tactics and much more.
So this platform, equipped with intelligence from FireEye’s front-line activities, will measure and verify companies’ security environments in terms of exposure to not only known but also new threats, allowing organizations to identify risks in security controls before a breach occurs and quickly adapt their defenses to the evolving threat landscape. In particular, Verodin will integrate with the security orchestration capabilities of FireEye Helix, but customers will also benefit from Verodin’s IT security measurement and validation solutions in an ‘as-a-service’ mode through the FireEye Managed Defense service and as part of the Expertise On Demand offering.
An ecosystem of partners investing in skills
“In Italy we are growing very well in terms of turnover, but above all in terms of the number of customers”. This is how Marco Riboli commented on the performance of the branch in Italy, a country characterized by the presence of many small companies operating internationally and with an important intellectual property to protect. Its sales channel is almost totally indirect, and in 99% of cases it works with specialised partners, to whom consultancy services are also delegated. “At a local level, we now have about 25 partners, four of which are Gold certified and twenty Silver, all with particularly strong characteristics in the security field,” says Luca Brandi, Channel Sales Leader Emea South Region of FireEye, who would like to underline that the Partner Program does not provide for the Registered level. “We are not interested in establishing occasional partnerships. We want to create strategic alliances, forging strong relationships with those who are really ready to invest in skills,” continues Brandi, recalling that FireEye certifications are free of charge.
Taken as a whole, all these choices have made it possible to build an extremely strong channel ecosystem in just a few years, which has even increased the vendor’s midmarket business by 200% in the first six years of 2019. To support the result, the entry of new specialized operators among the ranks of accredited companies and the development of skills among those who were already active in the territory. Said David:
The support of our two distribution companies, Arrow and Exclusive Networks, is fundamental in this sense: two value distributors who are very active on the education front with their own labs and are always ready to make certified resources available to their partners to create demos and Poc.
And, I should point out, the recent change to the licensing model, which today is no longer tied to configurations, but only to the number of users, also accelerates its entry into the Italian midmarket realities.
Luca Brandi, Channel Sales Leader Emea South Region of FireEye, finished off the event with the following:
What has always differentiated FireEye in this market have been technology, intelligence and the level of experience in victimology. We are the first company that has tackled cybersecurity through sandboxes and we have 200 consultants scattered around the world able to enter the dark web, deep web and hack community to anticipate what will be the next directions of attack. We have the indisputable ability to identify the threats Zero-Day, half of which are now identified by FireEye alone or in collaboration with Google and Microsoft.
I’ll close off this report with a video, our interview with David earlier this year at Le Fic where David chatted about the trend toward “security led by intelligence”, FireEye’s innovative “Expertise On Demand” which enables organizations to augment their security teams with FireEye’s frontline experts, the “FireEye Innovation Cycle” … oh, and lots of other cool stuff. Enjoy: