A hack leads to massive data leak from the Bulgarian National Revenue Agency (NRA). The alleged hacker claims he’s Russian, calling the government “mentally retarded”
17 July 2019 (Chania, Crete) – After a massive hack in Bulgaria, the prime minister called the attacker a “wizard,” but cybersecurity experts said the security was simply inadequate.
The hack: A 20-year-old man has been charged with an unprecedented hack of the country’s tax authority in June, ending with the theft of sensitive personal records from nearly every adult in Bulgaria. The data leak includes names, addresses, income and earnings information, and personal identification numbers, totaling 21 gigabytes and extending back over a decade. Initial estimates are that just under 11GB of that data have been leaked so far.
Nope, not a wizard: Security professionals say the SQL injection attack would have been easy to detect and exploit. Or to quote my favourite Bulgarian cyber follow on Twitter, the attacker left “a fuck ton” of digital traces that led to his arrest.
The consequences: The scope of this attack is vast, and the number of unanswered questions remains significant. We don’t know whether an individual, a group, or even a nation-state was behind it. Few believe the “lone hacker” story. Criminals, activists, and governments use hacked data in very different ways.
I spoke to one of my cyber security partners who was asked to analyse the case for one of his clients and he shared with me some of their analysis of the stolen 57-folder data mass that contained all of the files. They opened databases with more than 1 million rows containing Personal Identification Numbers, names, addresses, and even earnings. Much of the information is old and reflects reports from more than a decade ago. In others, it can not be determined at what point the data is dated. But some of the files contain new entries from June 2019, which suggests at least one breach was made recently.
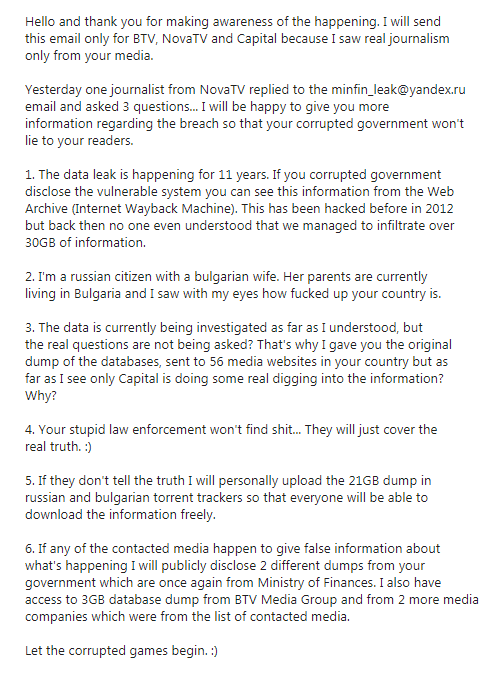
Following the attack, an email was sent to several Bulgarian media outlets in which the alleged hacker said he was a Russian citizen and that his wife was Bulgarian (see below). The only evidence of the alleged perpetrator being Russian is that the email address used came from the Russian domain Yandex.ru, which proves absolutely nothing since every single person on the planet with access to the Internet, with or without a VPN, can get a Yandex account.
In addition to an earlier message “your government is mentally retarded and your cybersecurity status is a parody” he sent the following email:
All cyber security analysts quoted in the media, and several I spoke with, said that the claim that a Russian hacker carried out the attack was suspect. We need to wait until the investigation is complete, and in cases of this nature there is always the possibility there was an “inside man.”
NOTE: there is some controversy over the man arrested for the hack. He was a researcher who tested computer networks for possible vulnerabilities to prevent cyber attacks. But he had also engaged in some criminal activity. Bulgarian media identified the suspect as Kristian Boykov, an employee at the Bulgarian office of U.S. cybersecurity firm TAD Group.
Boykov had posted regularly on social media about cybersecurity and hacking news before his arrest. In 2017, he made national news after exposing flaws in the Bulgarian Education Ministry’s website, work he then described as “fulfilling my civic duty” in a television interview.
Further, besides the NRA-specific information, other info appears to have been imported into NRA systems from other Bulgarian government agencies. The leaked data also contained information from Department Civil Registration and Administrative Services, a database the government described “similar to the Social Security Number (or similar) identification in other countries”. Information was also found that belonged to Bulgaria’s customs agency, namely data from the Bulgarian Excise Centralized Information System, a database for storing information about excise taxes for imported goods. In addition, there was also some information that local media deemed to have belonged to the National Health Insurance Fund, although they have not detailed the precise nature of the information, and data from the Bulgarian Employment Agency.
The cold truth: I am told the NRA is one of the most technically advanced administrations in Bulgaria. But as Bozhidar Bozhanov, chief executive at cybersecurity firm LogSentinel, said in several interviews today:
“The reason for the success of the attack does not seem to be the sophistication of the hacker, but rather poor security practices at the NRA. This issue appears to be the entire stack of technologies and services inside were not secure and the breach hints that few operational-security best practices were followed.”
The big open questions include who was behind the attack, and whether it was an individual, a group, or even a nation-state. Criminals, activists, and governments use hacked data in entirely different ways that can spell distinct forms of trouble for the Bulgarians affected by this breach. But one thing is clear: a reckoning has arrived for Bulgaria’s cybersecurity. Whether the government recognizes it or not, outside hackers certainly will.