[ Pour la version française, veuillez cliquez ici ]
10 April 2019 (Brussels, BE) — As I have noted before, the content (and conversations) available at an event like the International Cybersecurity Forum in Lille, France (hereinafter referred to Le FIC) can be enormous. When you have the brain power in attendance at an event like Le FIC, you cannot help but have deep conversations on all aspects of technology, not just cyber … subjects you tend not to address at other conferences. So you need to grab these brilliant people, these fabulous communication channels … folks like Michael Daniel, John Frank, David Grout, Pascal Le Digol, Philippe Dubuc, Colonel Cyril Piat, to name but a few.
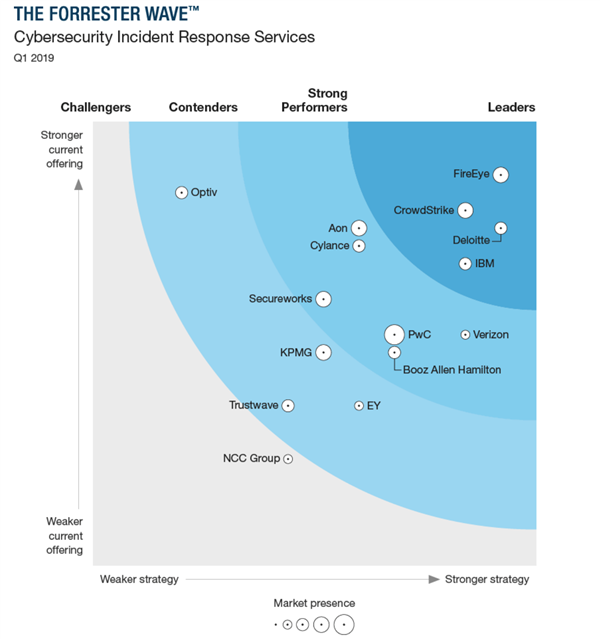
This post is about one of those cyber security mavens, David Grout … Chief Technology Officer for FireEye’s EMEA operations. FireEye is one of the leading world-wide cybersecurity companies providing hardware, software, and services to investigate cybersecurity attacks, protect against malicious software, and analyze IT security risks. And in fact it is the leader in cyber security incident response services.
I have known David for several years and he is simply a fount of knowledge on artificial intelligence, nation state hacking groups, critical infrastructure and utilities being targeted by cyber attacks, financially motivated cybercrime … oh, the list goes on and on. He is one of the most “in demand” speakers at Le FIC, and countless other cyber security events. It was David who introduced me to the concept of “supra threat actor” which describes threat actors that represent multiple countries, institutions or groups.
I also stay up-to-date via “M-Trends” which are based on FireEye Mandiant frontline investigations: reports on high-interest, significant cyber attacks across multiple industries and regions.
Most bizarre : several ransomware cyber attacks against cable car operators in Austria and Russia. Beyond the control of critical data, the attackers had the opportunity to take control of the targeted cable cars. And it highlights the vulnerability of many control systems. All cable cars are based on industrial control systems that ensure the safety of passenger and freight transport in real time. Perfect vulnerability to exploit for ransomware attacks. Cable car operators cannot afford any downtime or safety issues.
And two weeks before FIC 2019, FireEye released its report “Global DNS Hijacking Campaign: DNS Record Manipulation at Scale”, an analysis of the contours of sophisticated cyber espionage attacks. It is brilliant because it goes into far greater technical detail than any similar vendor report on the “how” of espionage campaigns.
In the following video, David hits the following points:
- Fortnite. With hundreds of millions of players world-wide, it continues to be the biggest on-line video game in the world. And it is full of dark cyber security issues.
- The trend toward “security led by intelligence”. You cannot defend against each cyber attack, secure all environments, using the same methods. You need to use intelligence to contextualise the attacker, to understand their knowledge.
- FireEye’s innovative “Expertise On Demand” which enables organizations to augment their security teams with FireEye’s frontline experts. It is literally threat intelligence and services at the click of a button: attacker insight, malicious code you need analyzed, more information on a cyber issue you read about, etc.
- FireEye’s #1 position in detecting zero-day attacks. A zero-day vulnerability, at its core, is a flaw. It is an unknown exploit in the wild that exposes a vulnerability in software or hardware and can create complicated problems well before anyone realizes something is wrong. In fact, a zero-day exploit leaves NO opportunity for detection … at first. Which is where FireEye comes in.
- And lastly, “The FireEye Innovation Cycle” which was created by FireEye product teams to match their world-class frontline threat expertise with frontline experts that can deploy immediate solutions. I have seen it in action and it is rather unique: it creates very effective cyber defense platforms – a seamless, sort of “on demand extension” of their customers security operations.
Enjoy the interview (with French and English subtitles):