
By:
Gregory P. Bufithis, Esq.
with major contributions by
Eric De Grasse, Chief Technology Officer
Alex Hania, Media Operations
Angela Gambetta, Content Manager
13 December 2016 (Paris, France) – Over the years I have been able to assemble a good cyber team from my existing staff. Eric and Alex have been attending events like Black Hat (in both Las Vegas and London) to develop an expertise on all elements of cyber security, as well as building an impressive list of both “white hat” and “black hat” contacts. Both have also completed several programs in the science and technology of cybersecurity and counterterrorism.
Angela has been with me for 10+ years taking on various roles across The Project Counsel Group. She is tasked with managing the firehose of “content” (as writing or video or photography is now called) we receive which includes … besides 32 hardcopy magazine subscriptions … a stream of 700+ websites we read/monitor. Her job is to find those info-nuggets in the myriad streams cascading on all of us … each individually tailored for relevance and accuracy. And she uses some funky AI developed by Eric.
My contribution is trying to see “The Big Picture”. Perhaps being an opsimath at heart and believing everything in technology is related, I undertake a conference schedule that provides me perspective and a holistic tech education. Call it my personal “Theory of Everything”. Although if you are not careful you can find yourself going through a mental miasma with all this overwhelming tech.
But for cyber security issues, it is a joy. I have memberships in such organizations as InfraGard (a non-profit organization serving as a public-private partnership between U.S. businesses and the U.S. Federal Bureau of Investigation) from which I benefit from a stream of information sharing and intelligence between businesses, academic institutions, state and local law enforcement agencies, and other intelligence community participants. That membership, coupled with my Linkedin intelligence community groups and ties to the Munich Security Conference, allows me to run a check on the many “cyber stories” that work through my network.
Over this past weekend I spent almost all day Friday, Saturday and Sunday reading up on the latest news on China’s hacking of U.S. law firms, and the Russian hacking of the U.S. political process and law firms … and many of the aspects of the geopolitics politics of this cyber war.
This past week the focus has been on:
1. a series of articles about cyber attacks across many U.S. law firms, most of them carried out by the Chinese government
2. the Russian hack of the U.S. political system, which at first blush reveals missed signals, slow responses and a continuing underestimation of the seriousness of a campaign of cyber espionage to disrupt the U.S. presidential race. The Russians have also dipped into U.S. law firms.
Herein is a mash-up of the main points:
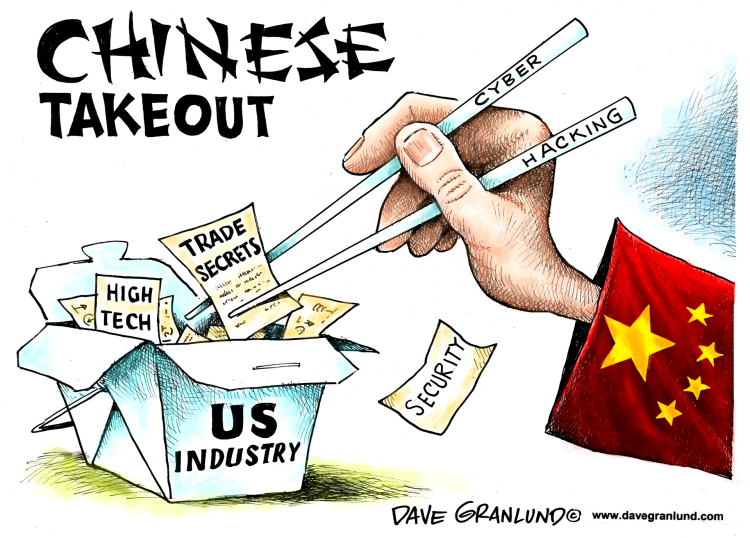
AH, THE CHINESE …
In the dark world of cyber-espionage, the finger of blame has often been pointed at China. Earlier this year, China’s cyber spies were accused of hacking into dozens of workstations and servers at the Federal Deposit Insurance Corp. Last year, Chinese hacking was blamed for the massive data breach at the US Office of Personnel Management which compromised the data of over 21 million people. As Michael Norwood, an analyst with FireEye, the dominant cybersecurity firm, told me:
“military intelligence has rapidly moved from cloak-and-dagger to bits-and-bytes over the last fifteen years. China has been developing masterful capabilities within the PLA [People’s Liberation Army] for a number of years, going back at least a decade. And their capabilities have now also been brought together into a single, strategic organization that is essentially a new branch of the military.”
FireEye had observed a significant change in Chinese cyber activity, almost a pivot towards Asia. They have seen more targeted attacks now focused on information gathering and intelligence collection from countries on the periphery of China — anyone with a land boundary or involved in a maritime dispute. And that kind of activity is much more focused on intelligence. But now with Trump about to get in the harness, all bets are off as to whether this recent pivot will be maintained … or retrained on the West.
I have had some delicious experiences as regards Chinese cyber warfare:
• I obtained my first full briefing on China’s “amazing, credible, super-sophisticated cyber attack capability” in May 2013 when Georgetown Law School launched its inaugural Cybersecurity Law Institute. I had been blogging about cyber security as a dominant feature of the global political agenda, and the industrial-scale theft of intellectual property by China. But it was at this conference that security experts made the humbling admission that the sophistication and evolution of the Chinese attacks were outpacing the defense.
• But the big take-away from that conference? No country has even come close to the U.S. in harnessing the power of computer networks to create and share knowledge, produce economic goods, intermesh private and government computing infrastructure including telecommunications and wireless networks, using all manner of technologies to carry data and multimedia communications, and control all manner of systems for our power energy distribution, transportation, manufacturing, etc. — and so left the U.S. as the most vulnerable technology ecosystem to those who can steal, corrupt, harm, and destroy public and private assets, at a pace often found unfathomable.
• That same year I heard a presentation by Stewart James (a partner with DLA Piper’s Intellectual Property & Technology Group). He talked about China’s “long game”, and how most lawyers do not understand how computer technologies have evolved, what they can do, so they have no clue as to the nature and scope of the threats. The Chinese are able to simply “walk into any law firm they wish”. For example, he ran through computer viruses that have evolved from simple programs easily detectable by anti-virus software to polymorphic programs that change with each new infection that are specifically designed to hide from screening technologies. He explained the development of the type of attack known as an “advanced persistent threat” or APT … a favorite of Chinese cyber attack teams. The effect of a virus is generally disruptive and experienced at the point (or soon after) the infection occurs but which can generally be resolved over a relatively short timescale (though the costs of doing so may still be considerable). By contrast, the aim of an APT is for the perpetrator to identify and exfiltrate valuable confidential information from the target site – attacks take time to develop and may be conducted over many months. For example, at a Mandiant workshop we learned how they were able to identify one attack that is reported to have taken about ten months to complete and extracted 10.5 terabytes of data from the target. This is truly industrial espionage, literally on an industrial scale. All of the confidential information that law firms gold is candy for the Chinese.
• And James spoke about an even bigger threat, that of small and medium-sized enterprises who are a more attractive target because they do not have the same protection in place as their larger brethren. They can still have large amounts of confidential information, including personal data, valuable intellectual property or sensitive commercial material that can be coupled with information from other sources to attack operational control systems.
• Then last summer I became indirectly involved when I was informed about an e-discovery document review in the D.C. Metro area involving a highly-complex intellectual property case. It was a “GAFA” case … GAFA being an acronym for Google, Apple, Facebook, and Amazon. Oh, and the acronym comes from the French. The term is widely used by the media to identify the 4 companies as a group, often in the context of legal investigations and litigations, but is now also used by the intelligence community to identify favorite targets of the Chinese:
• I was permitted to see the whole process used by the Chinese (I signed an NDA do I cannot provide specific details). Data was being pulled off the document review platform by review attorneys using flash drives (shades of Edward Snowden). As is the case in so many of these situations, it was the absence of any supervisory staff at the review center (a common event). And actually, the situation was observed and reported to us by several Posse List members on the review in the hope we’d report it to the law firm and keep the other reviewers out of the picture, which we did. Such extraction should not be possible in any such review tool but it was discovered that the security and audit controls around the e-discovery services process was defective and easily compromised (there was also data exfiltration via cyber means). What happened to the data I never determined. As we all know in these cases, law firms are notoriously close-lipped about data breach, and generally don’t report them at all.
This past week I summarised the articles I had read and the Chinese attack referenced above and discussed all of it with a few of my cybersecurity/cyber attack experts and they made the following points:
1. Everybody agreed that the law practice areas of those partners attached (mergers and acquisitions, intellectual property, etc.) certainly suggests the goal was economic theft.
2. But many wanted more details. For instance, very often a cyber attacker will build a profile on you, and will then lure you in. And leave “loitering munitions” (borrowing the Army phrase) so they can go back into a system at will. A recent case involved a “arbitrary command injection”. A command injection is an attack in which the goal is execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) The exploitation of the flaw is quite simple: the attackers just need victims information into visiting a website that contains specially crafted malicious code to trigger the vulnerability. One of our contacts dealt with a case where the user visited a specially crafted web site, a remote attacker then executing arbitrary commands. The attacker had a profile on the user and created a site that he suspected the user would visit. How often were these being used? Impossible to say but my cyber contacts say it is standard operating procedure for both the Chinese and the Russians. And the “injection commands” are getting more sophisticated. So the assumption is that the attacker can go back in and, in effect, “upgrade” his attack software.
3. Another hacker (a “black hat”) told me how attackers can install skimming scripts on online stores and compromise hundreds of thousands of credit cards and personal information. This was apparently used by the Chinese to compromise the U.S. National Republican Senatorial Committee store.
4. In the glare of the spotlight that falls on human fraud, phishing, malware, adware, spam, blended threats, DoS attacks, etc., hitherto innocuous endpoint devices such as printers are not recognized as a large enough threat. Peter Kim, who is an industry-leading penetration tester/hacker who writes extensively about penetration testing has noted numerous times how easy it is to execute cyber fraud by explaining that he has compromised several companies using just printers to gain an initial foothold. Four of the cyber experts I chatted with had “no doubt” that was a major way into law firms … a method I actually noted back in 2013 in my write-up of the Georgetown Law conference. One of my contacts said that in 2015 he worked on a law firm case where “we found a laser printer at the firm sending out a stream of SSL traffic in a security breach on the network”. Meaning someone was accessing whatever was on that printer (and probably more) unimpeded.
5. “The Starbucks Hack”. Many of my contacts told me the FBI tracked Chinese hackers using the well-know “Starbucks hack” on a law firm which I also wrote about last year. It goes something like this:
• You are working on a (highly confidential) brief/memo, you need a break, you grab your laptop and pop out of the office with your working partner and head over to Starbucks to work on it.
• And your laptop is hacked. Happens all the time.
• About 4 years ago Starbucks offered free Wi-Fi in all of its U.S. locations to compete with McDonalds who had been offering it for some time. Cybercriminals took note. Exposure to identity theft, account password compromise and and data access led to skyrocketing cybercrime.
-Note: in a conversation with the Starbucks public relations office we learned that, on average, laptop users spend about 2.5 hours using the wireless internet in Starbucks stores while mobile phone users who can use Wi-Fi spend about 2 hours on the network.
-In the U.S., hotspots range from paid services (such as T-Mobile or Verizon) to public/free connections (often through AT&T but “branded” under a trade name; see paragraph below). But they all have one thing in common: they are open networks that are vulnerable to security breaches. Because they do not encrypt data, your passwords, email messages, and other information can be visible to hackers.
-In Washington, DC there is a stretch of K Street that is home to a Starbucks, a FedEx Office, and several restaurants. They all use the AT&T wireless service, branded under their trade name. Zack L (a “black hat” friend who shall remain anonymous) showed me how he could take over the wireless connections and feed the information to his laptop. He also used something called “Cain & Able” which is a multi-purpose tool that can intercept network traffic, using information contained in those packets to crack encrypted passwords using dictionary, brute-force and cryptanalysis attack methods, record VoIP conversations, recover wireless network keys, and analyze routing protocols. He says the Chinese use tools “far more sophisticated”.
-It is what Zack calls a “wireless Honeypot attack”. In brief: normally, when a wireless client (PC, Laptop) is switched on, it will try to probe the nearby area for access points for a particular SSID (SSID is like a name for the network, which is advertised in order for users and clients to associate with the access points). In this scenario, if a hacker is nearby (perhaps in the Starbucks), he could use access points with high power (gain) antennas with the same SSID as the corporate network SSID and respond to such client probe requests with a valid probe response. As the wireless clients generally associate with an access point with the highest power (signal strength), it can get associated to the access point belonging to the hacker. Once the honeypot association is made by the attacker with a valid client from an internal corporate network, he can find out a lot of information about both the client and the network and use them to launch further attacks like a “Man In the Middle” attack. So the wireless honeypot itself is not an attack but it paves the way for other attacks.
-And a “Man In The Middle” (you’ll see MITM in all of the literature) attack is actually a continuation of the honeypot attack wherein a hacker would lure a wireless client to associate with his honeypot access point (either by increasing the honeypot access point’s signal strength using high gain antennas (or) by inducing a denial of service attack on the nearest legitimate AP with the highest signal strength) and utilizes his laptop/computer as a proxy server where all the communication between the wireless client (user) and the target host server goes through this proxy server. Initially, the target host server would be a public server placed on the Internet but if proper information is available, it could be an internal server as well.
[NOTE TO READERS: “The Starbucks Hack” is still being used]
6. But tips galore from the group on working out-of-the-office/on-the-road … securely … from wireless hotspots:
-Disable your Wi-Fi adapter. When you’re not at home or at work, it’s a good idea to turn off your laptop’s Wi-Fi capability when you’re not using it. Otherwise your computer might connect to a malicious hot spot without your realizing it. Most laptops now have a Wi-Fi hardware button you can use to disable your Wi-Fi adapter or a simple disable function using your operating system.
-Try to choose more secure connections. Use a virtual private network (VPN). It’s not always possible to choose your connection type, but internet security is critical. When you can, opt for wireless networks that require a network security key or have some other form of security, such as a certificate. The information sent over these networks is encrypted, and encryption can help protect your computer from unauthorized access. For example, instead of using a public hot spot with no encryption, use a VPN. If your law firm or company does not have its own VPN, you can download and install free VPN software. The security features of the different available networks appear along with the network name as your laptop discovers them.
-Protect your email with https. One way to protect your email messages in public is to select the “https” or other secure connection option in your email account settings (if your email provider supplies one), or something similar. Even if the email provider you use has a secure network, after you log on to your account on a public network, your information is no longer encrypted unless you use a more secure connection. An “https” connection, for example, which includes encryption, is more secure than an http connection
-Make sure your firewall is activated. A firewall helps protect your laptop by preventing unauthorized users from gaining access to your computer through the internet or a network. It acts as a barrier that checks all incoming information and then either blocks the information or allows it to come through. All Windows operating systems come with a firewall, and you can make sure it’s turned on. Apple and Android iOS also have firewall apps. Some antivirus software includes its own firewall.
-Monitor your access points. Chances are that there are multiple wireless networks anywhere you’re trying to connect. These connections are all access points, because they link into the wired system that gives you internet access. So how do you make sure you’re connecting to the right one? Simple—by configuring your laptop to let you approve access points before you connect.
-Disable file and printer sharing. File and printer sharing is a feature that enables other computers on a network to access resources on your computer. When you are using your mobile laptop/device in a hot spot, it’s best to disable file and printer sharing. When it is enabled, it leaves your computer vulnerable to hackers.
-Make your folders private. When the folders on your mobile device are private, it’s more difficult for hackers to access your files.
-Encrypt your files. You can protect your files further by encrypting them, which requires a password to open or modify them. Because you must perform this procedure on one file at a time, consider password-protecting only the files that you plan to use while working in a public place.
And yes, I am aware of the efforts being made by such companies as EMC, HP, IBM Watson, Symantec, etc. to take an “intelligence-driven information security” approach and “cognitive security” approach. The security information and event management (SIEM) market is enormous. This includes the consistent collection of reliable cyber-risk data from a range of government, industry, commercial, and internal sources to gain a more complete understanding of risks and exposures, plus ongoing research on prospective cyber adversaries to develop knowledge of attack motivations, favored techniques, and known activities. Interesting stuff but for the moment I shall take the cognitive solutions approach with a grain of salt.
OH, AND THOSE RUSSIANS …
At its most simplest, the story of how Russia won the (first) Russo-American cyberwar is because Obama did not fight back and failed to protect America’s democracy from Putin’s well-orchestrated, wide-ranging cyber assault. Obama’s maddening naiveté … manifesting hardly for the first time during his presidency … demonstrated how poorly he understood his adversary, and unsurprisingly, Putin was emboldened on so many fronts.
Well, that and not understanding the Russian dynamic. At the European Electronic Warfare Symposium this year, one of the best presentations was by said Dr. David Stupples, director of the Centre for Cyber Security Sciences at City University London. He made several points but here are the key ones from the presentation:
1. Russia’s intelligence services decided years ago to make cyber warfare a national defense priority. They have become increasingly proficient in cyber operations as a result.
2. From around 2007, Russia decided that information warfare was key to winning any world conflict, and that it was this area of capability and technology they decided would benefit from vastly increased military investment. What made this decision easier was that Russia was also home to the largest numbers of some of the world’s best hackers.
3. The Democratic National Committee (DNC) was obviously not a high-value military target but it served a threefold motivation to hack its system: (i) demonstrate that Russia is on top of its game in this kind of shadowy warfare; (ii) embarrass the Democrats and undermine the presidential election process; and (ii) test U.S. security measures.
4. This testing goes on all the time. Testing U.S. defenses would reveal to Moscow how Washington might react in response to further provocations. The goal of testing U.S. security measures is not now, nor has it in the past, proved to be a difficult objective for Moscow, The National Security Agency and FBI have both admitted that Russia had penetrated a significant number of sensitive U.S. infrastructure systems in order to test efficacy and document structure. I would surmise also to steal military secrets.
Read any of the major defense/cyber security journals … for example, Defense One or Cyber Brief … and you come away with a key point: Russia’s cyber warfare activities are not just random disruption or embarrassing revelations. What Russia is doing is linking cyber attacking and hacking with its open information warfare methods … propaganda disguised as news programming, funding of NGOs, etc., etc. … and in coordination with its military establishment’s use of electronic warfare. By employing all three methods together in an integrated pattern of activity Moscow can achieve what its military theorists call “reflexive control” — in other words warping your adversary’s perceptions to the point where that adversary begins to unknowingly take wrong or damaging actions.
And Russia has a distinct advantage in the cyber realm because on a regular basis it engages the services of non-governmental cyber crime entities, which masks its role in cyber attacks. This is what the U.S. and others do not do — engage proxy cyber warriors. This is not to say we never use them. But as explained to me by Linda Nowak of Crowdstrike:
“What the Russians are saying is that we will make these criminal organizations our partners — recruiting them to do cyber work for the Russian state. The Kremlin promises its criminal partners it will turn a blind eye to their attacking banks, disrupting commerce in the West, stealing money, etc. so long as they make themselves available to do the odd job for Russia’s intelligence services and military”.
A presenter from NATO intelligence said they believe there are currently more than one million Russian programmers engaged in cyber crime. These programmers are affiliated with 40 Russian-based cyber crime rings. The United States and its partners could not feasibly match this level of manpower using only government agencies and employees.
Note: Crowdstrike is at the forefront of threat intelligence and incident response. It was their analysis of the code and techniques used against the DNC which resembled those from earlier attacks on the White House and the State Department that led them to identify not one but two Russian intruders, names you have all heard in the media: Cozy Bear, which is believed to be affiliated with the FSB, Russia’s answer to the CIA; and Fancy Bear, which they had linked to the GRU, Russian military intelligence.
And let’s be very clear. Russian spies did not, of course, wait until the summer of 2015 to start hacking the United States. This past fall, in fact, marked the twentieth anniversary of the world’s first major campaign of state-on-state digital espionage. In 1996, five years after the end of the USSR, the Pentagon began to detect high-volume network breaches from Russia. The campaign was an intelligence-gathering operation: whenever the intruders from Moscow found their way into a U. S. government computer, they binged, stealing copies of every file they could.
By 1998, when the FBI code-named the hacking campaign Moonlight Maze, the Russians were commandeering foreign computers and using them as staging hubs. At a time when a 56 kbps dial-up connection was more than sufficient to get the best of Pets.com and AltaVista, Russian operators extracted several gigabytes of data from a U. S. Navy computer in a single session. With the unwitting help of proxy machines—including a Navy supercomputer in Virginia Beach, a server at a London nonprofit, and a computer lab at a public library in Colorado—that accomplishment was repeated hundreds of times over. Eventually, the Russians stole the equivalent, as an Air Intelligence Agency estimate later had it, of “a stack of printed copier paper three times the height of the Washington Monument.”
To understand all of this and to give this “new face of warfare” perspective, first a bit of a polemic, and then my cyber analysis:

To fully understand the danger to law firms, the FBI believe the attacks began in earnest in 2012 and have not stopped, and will not stop. They are easy targets, and when they do put up a “defense” it is easily defeated. Law firms seem to refuse to pay the cost of bringing in the right experts and assets to stop attacks.
On the political side, American spy and law enforcement agencies are united in the belief that, in the weeks before the U.S. presidential election, the Russian government deployed computer hackers to sow chaos during the campaign. But they had conflicting views about the specific goals of the subterfuge. Last week, Central Intelligence Agency officials presented lawmakers with a stunning new judgment that upended the debate: Russia, they said, had intervened with the primary aim of helping make Donald J. Trump become president.
The C.I.A.’s conclusion does not appear to be the product of specific new intelligence obtained since the election, several American officials, including some who had read the agency’s briefing, said on Sunday. Rather, it was an analysis of what many believe is overwhelming circumstantial evidence — evidence that others feel does not support firm judgments — that the Russians put a thumb on the scale for Trump, and got their desired outcome.
It is unclear why the C.I.A. did not produce this formal assessment before the election, although several officials said that parts of it had been made available to President Obama in the presidential daily briefing in the weeks before the vote. It is said Obama did not want to appear he was acting politically in favor of Hillary Clinton, and so he called in Congressional leaders to act on the interference. The Dems were ready to go, but Mitch McConnell dissembled. He said it was “political.” Wow, big surprise. And after the election, Donald names McConnell’s wife Transportation Secretary and denies any Russian shenanigans.
But the conclusion that Moscow ran an operation to help install the next president is one of the most consequential analyses by American spy agencies in years. And over the last 8 years, having looked at almost everything through a geopolitical prism, I know the dispute cuts to core realities of intelligence analysis: judgments are often made in a fog of uncertainty, are sometimes based on putting together shards of a mosaic that do not reveal a full picture, and can always be affected by human biases. And truth is always the first casualty of many Americans’ emotional reaction.
And having lived through it, I cannot help but see the analogy to the Watergate break-in June, 1972. The media let it slide (except the meticulous coverage by the Washington Post). We held the election and Nixon won. Later, he had to resign because of the story that broke months before the election.
Comes now … “Russiagate”!!
Going back to the Soviet Union era, for the KGB, the predecessor to the SVR, the FSB – the organizations Putin rose up through – the U.S. is the main enemy. We’ve been the main enemy since World War Two, and we continued to be the main enemy through the Cold War and into today. We’ve seen it in the ‘90s and the 2000s. We’re the main enemy and we’re the greatest rival they have for world influence. So to me, none of what has happened is unexpected.
One of the key points made this fall at one of the Munich Security Conference follow-ups (the full event is in February, with follow-ups in September and November) was that Russia is extremely patient, more so than their American counterparts, when it comes to espionage. Rob Richer, former CIA Associate Deputy Director for Operations and formerly chief of Russian Operations, noted that when he was chief of Russia operations from 1995 to 1998 it was at a time when the CIA was catching Russia’s long term penetrations of the CIA, of the FBI, of NSA, and of the U.S. military. There are numerous books on this period. Richer noted some of those people were developed over time. The Russians have no problem looking five, ten years down the road. The U.S. government tends to look at things in two to three year windows.
Richer gave this example: a CIA case officer arrives at a new station. His job is to recruit spies; he recruits them. That’s where he gets his credit. He turns them over to someone else. The handler doesn’t get as much credit as the person who has recruited the spy. The CIA is continually turning people over and looking for short-term gains. Whereas the Russians will have someone handle a guy for 10, 12, 15 years. The CIA keeps bumping into him.
But this “short-termism” is in so much of American culture. Americans live in political cycles and in assignment cycles. Every four to eight years, we have a new presidency. If you look at Congress, you look at the Senate, you look at Intelligence Oversight. There’s a high rate of turnover. And in the CIA you get a new director every administration. Each time, they have a different agenda.
The Russians put someone in charge of an intelligence service for more than a decade.
Yes, technology and the ability to manipulate the web and develop hacking skills – that’s modern history of the last three, four years. That was a game changer. But what did we do? The Western intelligence community spent billions to spy on everyone, while Russia stayed focused. The West turned into what they previously despised and feared (a surveillance state), while Russia stayed focused on getting their ducks in line: further developed their human intelligence assets, further developed their targeted cyber-ops capability, showed off their developed weaponry in Syria, etc. And Putin made brilliant use of old and new forms of propaganda to exploit political divisions. The leading element of this has been RT (Russia Today) which is not only one of the most widely watched (and heavily subsidized) global sources of state television propaganda (which claims 70 million weekly viewers and 35 million daily) but a vast social-media machinery as well. Added to its hidden influence is a vast network of Russian trolls — agents paid to spread disinformation and Russian propaganda points by posing as authentic and spontaneous commentators.
We always, always, always make the mistake of treating Russia as if it were backwards. Russia wants to be an equal world power, if not the world power. Putin in many ways thinks like a Czar. He wants that authority. He wants that control. So they set a goal to be able to influence things in the United States, whether politically, using firms to lobby or through business deals.
Look at Syria. Does Putin really care about Syria? Of course not. Does he care about being a main player in the Middle East and showing that he has the clout to push the U.S. back? Yes, and that’s what he’s done. Look at Ukraine. This is more about the politics of presence and influence, than about the politics of actually what happens.
And do not discount the “fear factor’. Since huge swaths of society rose up in color revolutions in the former Yugoslavia in 2000, in Georgia in 2003, and in Ukraine in 2004-2005 — all to protest electoral fraud and bring about a transition from authoritarianism to democracy — Putin has behaved as if obsessed with fear that the virus of mass democratic mobilization might spread to Russia itself. Neither was he prepared to condone the “loss” of key parts of the former Soviet Union, such as Georgia and Ukraine, to any potential alliance structure with the West.
The U.S. is now a step back … far back. It must now accelerate its intelligence gathering on Russian intentions. That is the hardest intelligence to collect. It has to actively recruit target officers, who have understanding of intent against America. Since 9/11, the focus has been on combatting terrorism. We flooded Afghanistan with officers, then reduced them. We flooding Iraq with officers, then reduced them. EVERYTHING was flavored by what was happening across the Middle East. Russia was a distant concern, particularly for the current administration, because they didn’t have strong relations with Moscow. They didn’t have a political dialogue. So they kind of thrust it aside and worried about the things that would kill Americans. And the thing that will kill Americans is terrorism.
Presidential Pensiveness and Paralysis
Despite all of the cyber attack information that Obama had, he steadfastly refused to publicly name Russia as the culprit, in part because of fears of igniting a conflict and uncertainty as to how to respond to such attacks. The most absurd part of his rationale … as reported in the New York Times … was that he was worried naming the Russians and taking a strong stance against them would harm John Kerry’s then-ongoing diplomatic efforts to win cooperation with the Russians on Syria, as all recent diplomatic talks with them on Syria had been a farce. The same officials noted that Obama feared additional cyber attacks by Putin, additional military harassment in the Black and Baltic seas, and further aggression in Eastern Europe.
Yes, incredulously, Obama imagined that turning a blind eye to Russian interference in domestic American elections would somehow invite Russian compromise on other fronts, frustrating some on his team. Brian Frydenborg, who writes for the Russian International Affairs Council, had a brilliant piece on this aspect and said in a bog post:
“I am reminded of the scene in ‘The Lord of the Rings: The Two Towers’, when the heroes are trying to convince Théoden, King of Rohan, to stand up for his people against the disinformation and aggression of Saruman; Théoden responds by saying “I will not risk open war,” to which Aragorn retorts “Open war is upon you, whether you would risk it or not;” in the real world, we had Obama playing the role of a Théoden in denial.”
In charge of a relatively weaker Russia taking on the most powerful nation in the world and regardless of the election’s outcome, Putin had already won: he took to heart von Clausewitz’s maxim that “War is the continuation of policy [or politics] by other means,” something that Obama seems to have missed. Putin had essentially “weaponized” WikiLeaks (and, in the process, the unwitting U.S. news media) against Clinton, the Democratic Party, the U.S. electoral process, and American democracy itself.
This is the new face of warfare, one in which the lines between politics and war are erased and in which Russia is dominant and ahead of everyone, and this should be terrifying all of us. But I am not going to write that this is a fatal blow for the U.S. or the West, but it is a grievous one, and that it is one that the public and news media seem unable to discover or acknowledge, let alone comprehend or respond to appropriately, makes it all the more dangerous and all the more likely to happen again … and again.
As I wrote last week, this is part of a larger Russian war against the West that is becoming increasingly brazen: until this year, Syria and Ukraine were the most glaring centerpieces in Russia’s disinformation campaigns. But Trump’s election and just this week, Russia’s tool WikiLeaks is already unleashing its might against Angela Merkel and her party in Germany, which fears far more interference in its 2017 national elections, and Russian propaganda was active in supporting the right-wing parties in Italy’s big vote that was a stinging defeat for it centrist pro-EU leader and his party. Additionally, Russia’s neighboring three Baltic states of Estonia, Latvia, and Lithuania—already subject to heavy Russian disinformation operations—have seen a significant increase in Russian disinformation since the U.S. election and many there fear what is to come next.
It’s a serious threat. Putin seeks to weaken the US, the EU, and NATO to the degree that they can no longer presume to call the shots without his agreement in international affairs. Since western governments are not ordinarily prepared for such stout challenges to their democracies, they are vulnerable to the weapons of doubt he is employing, mainly creating the impression that there are no indisputable facts, that anything could be true, and that everything is either already compromised, or could be. Since trust is the bedrock of democracy, this threatens social stability across the West.
SO WHAT DOES THE U.S. DO?
Of all the documents leaked by Edward Snowden the ones most interesting were those that detailed how the U.S. government was building up an enormous arsenal of cyber capabilities, and at times using them. In 2013, the Washington Post reported from the Snowden disclosures that the U.S. government carried out 231 offensive cyber operations in 2011, none of which came near the level of the now famous “Stuxnet” attack.
Granted, much of those Snowden documents are out of date. But most everyone I speak with says the U.S. has the most powerful cyber arsenal in the world, some using the example of the North Korean Internet collapse in December 2014, when the nation’s Internet went out for 12 hours, just a few days after the White House blamed the Sony hack on Pyongyang.
And many tell me about a cyber weapon called a “capability” in the field which is a piece of malicious code that exploits a flaw in an enemy’s software; the point is to manipulate, disrupt or destroy computers, information systems, networks or physical infrastructure controlled by computer systems. An attacker could use a cyber weapon to take down another country’s financial systems or electrical systems. Most believe the U.S. excels at this.
But the Snowden leaks also revealed the dilemma in internal government discussions: we have a current state of affairs extremely volatile and unstable because one could escalate a cyberwar pretty quickly. At the moment, cyber experts say, the world is at a tenuous moment of cyber peace. For all the constant theft and hacking, nobody is waging overt attacks on infrastructure and assets. But they also say this relative stability masks the underlying threats in the cyber world. Brandon Valeriano, a lecturer at the University of Glasgow who focuses on cyber conflict and is a fountain of information, says we’re in a cold war, not a peace. If you paint a picture of the world above, people are shaking hands. And then below the water, they’re kicking like crazy. In cyber there’s so much going on but it’s invisible to most people.
Ok, it seems we do suck at defense. But the US has the most advanced offensive cyber capability on the planet. It has been reluctant to retaliate out of fear of triggering a dangerous, all-out global cyber conflict. But it’s clear that the US will have to do something to show Putin that two can play this game. One would think an option is to out him on his presumed personal wealth, with details of all his homes, property, and hard cash. Or the Internet can be shut off to important government or personal facilities or homes. What the US likely won’t do is to launch a debilitating attack, such as temporarily taking out the Moscow electric grid. That would go beyond the realm of mere mischief and into the risk of tit-for-tat warfare.
Bottom line: if a major cyber incident occurred in the U.S. — one that actually hurt or even killed Americans — the public would quickly want some answers, and likely a plan for defense and retaliation. In the absence of more specific rules of engagement, it’s clear to many experts what’s going to happen at this point: we’re going to improvise and somebody is going to overreact. Until then, as Brandon Valeriano says, below the water there is a lot of crazy kicking going on.


One Reply to “THE LONG READ: the Chinese violate U.S. law firm data security, and the Russians hack the U.S. political process and law firms. Oh, the geopolitics of cyber war!”