[ Pour la version française, veuillez cliquer ici ]
To my “Le FIC” readers: full coverage of FIC 2020 (including video interviews and vendor summaries) will begin to roll out next week
18 March 2020 (Brussels, Belgium) – As I noted in my cyber newsletter yesterday, the U.S. Department of Health and Human Services (HHS) claims it was attacked by hackers this past weekend as the agency was ramping up its response to the coronavirus pandemic. The cyberattack, first reported by Bloomberg News, involved hackers accessing HHS’s systems on Sunday night. According to Bloomberg, they were not able to steal anything, and the goal was to slow down systems. HHS spokesperson Caitlin Oakley:
“HHS has an IT infrastructure with risk-based security controls continuously monitored in order to detect and address cybersecurity threats and vulnerabilities. On Sunday, we became aware of a significant increase in activity on HHS cyber infrastructure and are fully operational as we actively investigate the matter. Early on while preparing and responding to COVID-19, HHS put extra protections in place. We are coordinating with federal law enforcement and remain vigilant and focused on ensuring the integrity of our IT infrastructure.”
HHS Secretary Alex Azar played down the hacking incident during a press conference later on Monday.
“We have extremely strong barriers, we had no penetration into our networks, no degradation of the functioning of our networks, we had no limitation on the ability or capacity of our people to telework, we’ve taken very strong defensive actions”.
Of course, being a cynic, could it have been normal traffic? It’s not like the present Sainted Federal Government has anything resembling clues when it comes to the proper care and feeding of an extremely well used web site. Looking at the way incompetence is blamed on others and the value of having a boogeyman for corralling the sheep, one should always take whatever any government, especially the ones that have lied time and again, with a huge bag of salt.
Although a cyber security client did inform me that an almost identical attack was launched over the weekend on the main university hospital Brno in the Czech Republic, so who knows.
But there is worse happening out there.
Exploiting coronavirus disruption
Cyber security firm Check Point has found that since January 2020 there have been over 4,000 coronavirus-related domains registered globally with 3 per cent found to be malicious and an additional 5 per cent suspicious. It has pointed out in a series of reports that cyber criminals and hacking groups are exploiting disruption caused by the coronavirus through a range of phishing and malware attacks which are likely to proliferate as the outbreak intensifies. This week, experts at the UK National Cyber Security Centre said web users are in danger of losing money and sensitive data if they’re tricked into clicking on links in bogus emails claiming to contain important information about the pandemic.
Note: the UK National Cyber Security Centre is a branch of the UK signals intelligence agency GCHQ. Government Communications Headquarters (commonly known as GCHQ) is an intelligence and security organization responsible for providing signals intelligence and information assurance to the government and armed forces of the United Kingdom.
Both Checkpoint and the National Cyber Security Centre have noted examples so far that include cyber scams by groups impersonating the World Health Organization and the U.S. Centre for Disease Control, fraudulent websites advertising antiviral equipment which turns out to be fake, and attackers seeking bitcoin funding which they claim is for vaccine research. These warnings come after the government said last week it had set up a dedicated unit to combat malicious coronavirus disinformation campaigns by hostile states or cyber criminals, and confirmed it is working with social media companies to refute false or misleading claims about the disease. Platforms such as Facebook and Twitter are working with the NHS to elevate official government sites to the top of search results relating to the virus.
While the NCSC is focused on cyber criminals looking to exploit the crisis for financial gain, others have suggested hostile states could be taking advantage of the confusion. The U.S. State Department issued a directive that said Russia was responsible for “swarms of online, false personas; entire ecosystem of Russian disinformation is at play in attempts to capitalise on uncertainty caused by the pandemic”. The Russians are very good at playing the zero sum game: whatever hurts my enemy, helps me.
Note: well, not that the UK needs the Russians. UK MPs continue to fire in Freedom of Information requests to the National Health Service which has been eating into the time NHS clinicians and managers have trying to deal with COVID planning. Is that a cyber attack?
The increase in the registration of web pages relating to the coronavirus suggesting that cyber criminals are likely to be taking advantage of the outbreak makes perfect sense. I spoke to John Hon, a security engineer at Checkpoint who told me:
As the virus spreads across the globe, people are naturally searching online for the latest information and updates on how it might affect them, and what they can do to protect themselves and their families. And as you might expect, cyber-criminals are quick to take advantage of these concerns for their own gain. We are seeing a trend, a malicious trend hidden inside a legitimate one. There are lots of real websites being registered, there’s a huge increase in websites on this topic. What’s concerning is that the number of malicious sites is 50% higher than we would expect.
As we recently reported, hackers around the globe have found the Coronavirus serving them well as an enabler for their activities, and are still riding the wave of the epidemic. Our Global Threat Index for January 2020 shows cyber-criminals are exploiting interest in the global epidemic to spread malicious activity, with several spam campaigns relating to the outbreak of the virus. Since January 2020, based on Check Point Threat Intelligence, there have been over 4,000 coronavirus-related domains registered globally. Out of these websites, 3% were found to be malicious and an additional 5% are suspicious. Coronavirus- related domains are 50% more likely to be malicious than other domains registered at the same period, and also higher than recent seasonal themes such as Valentine’s day.
Some individuals in the UK have already been targeted by coronavirus-themed phishing emails with infected attachments containing fictitious safety measures. Researchers at the cyber security company Proofpoint, which has been working with the UK government, told me such attacks have recently become more targeted, with greater numbers focusing on the supply chain impact of the virus on sectors such as shipping, transport and retail.
Here is a shot from a malicious doc file found across UK systems:
Clicking on “enable editing” and “enable content” will lead to the download of Ostap Trojan-Downloader, which is known to be a Trickbot downloader. Trickbot is a dominant banking Trojan constantly being updated with new capabilities, features and distribution vectors. This enables Trickbot to be a flexible and customizable malware that can be distributed as part of multi purpose campaigns.
There is also one big issue that all cyber security analysts are finding: with the need to set people up with new laptops in a hurry to meet the need for working from home, employers are taking shortcuts in their cyber security protocols, prompting concerns that companies may be more vulnerable. A computer reseller in the U.S. and one in the UK told me many large companies are buying brands they would not normally use in order to get hold of stock and that they are not conducting the usual rigorous testing procedures before buying the laptops.
The targeted Italian phishing campaign
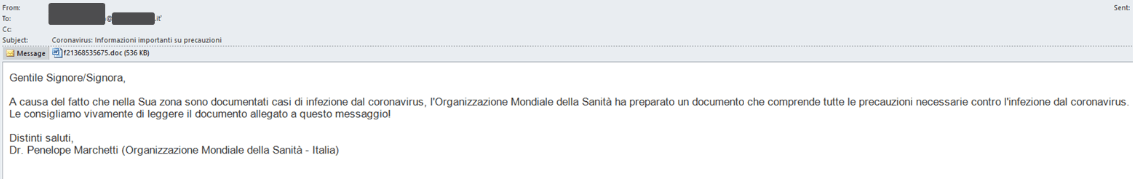
In addition, special attention has been paid to Italy where a widespread targeted coronavirus themed phishing campaign was spotted targeting Italian organizations, hitting over 10% of all organizations in Italy with the aim of exploiting concerns over the growing cluster of infections in the country. Check Point, FireEye and Sophos have all seen this. Here is an example of the mail content:
English translation:
Due to the number of cases of coronavirus infection that have been documented in your area, the World Health Organization has prepared a document that includes all the necessary precautions against coronavirus infection.
We strongly recommend that you read the document attached to this message.
With best regards,
Dr. Penelope Marchetti (World Health Organization – Italy
The email contains a malicious document file, named f###########.doc (#=digit) and with the email subject “Coronavirus: Informazioni importanti su precauzioni” (English translation: Coronavirus: Important information about precautions), and the email is signed off by a doctor from World Health Organization (WHO) based in Italy. However a search online does not find a doctor by the name of Penelope Marchetti with WHO or Organizzazione Mondiale della Sanità (OMS). Also, the senders’ email addresses are not from official WHO or OMS domains, and most of them were not Italian at all.
The research team at Sophos has warned of the same campaign, pointing out that they have seen “other payloads from the same spam-generating malware dating back to September of last year – which also carried malicious documents, carried a different variety of concern-inducing calls to action, with subject lines such as ‘you have email about your credit’ and ‘you have received fax about your loan'”. In an alert, Sophos warned :
“While this is in Italy now, we would expect similar attacks in other countries where fears of COVID-19 outbreaks are high. We must stay vigilant and be distrustful of incoming communications during times of crisis and only obtain advice from our public health authorities.”
As David Grout of FireEye noted:
We can all expect to be inundated with malware-laced emails and texts as well as nuisance spam linked to coronavirus. It’s too fertile a hunting ground for an attacker not to use. As we Google and share messages with friends and family and look for the latest news and information, it’s easy to slip something malicious into the mix.
And the dragon is hardly sleeping through all of this
Forbes, The Verge and Blooomberg News have all reported on this, and both Check Point and FireEye have issued “target notices” so here is a mash-up of all their most salient points.
As I noted above, we have seen multiple stories about coronavirus-related information being used to disguise malware-laced messages and apps, which are now being distributed by threat actors around the world. Chinese state-sponsored hackers are keen to get in on the act – at least according to the team at Check Point. In a research published over the weekend and updated today, the firm exposes a Chinese APT, which it says has “weaponized” documents “to deliver previously unknown malware.” Check Point says its research team had intercepted “a targeted cyber-attack by a Chinese APT group on a public sector entity of Mongolia.” An attack which “leveraged the coronavirus pandemic.” In this example of social engineering at the highest level, the APT sent two documents, “one related to COVID-19, both impersonating the Mongolian Ministry of Foreign Affairs in the form of press briefings.” Those documents contained unique, remote access malware.
Again, the tip of a nasty iceberg, as hackers target a world of people concerned about their health and finances with coronavirus escalating into a global crisis. At one point I simply lost track of every cyber analyst issuing reports on every scum rapidly registering vast numbers of potentially-malicious websites and sending out masses of scam emails as they try to make money from the pandemic.
This particular Chinese APT coronavirus document, Check Point says, “was entitled ‘About the Spread of New Coronavirus Infections,’ and cites the National Health Committee of China.” In its summary Check Point noted:
We have now seen multiple malware attacks framed under similar advisory notices—this is the first, though, that can be attributed to state-sponsored hackers in a campaign against an overseas government.
This is the latest iteration of what seems to be a long-running Chinese-based operation against a variety of governments and organizations worldwide. This specific campaign was leveraging the COVID-19 pandemic to lure victims to trigger the infection chain.
The attack was “exploiting public interest in coronavirus for China’s own agenda through a novel cyber infection chain. The group has been targeting not just Mongolia but other countries world-wide. All public sector entities and telcos everywhere should be extra wary of documents and websites themed around coronavirus.
These malware-laced documents appeared to come from Mongolia’s government, with a least one purporting to be from the country’s Minister of Foreign Affairs. The targets were other elements of Mongolia’s public sector, with the objective to take screenshots, exfiltrate, delete and edit files, and remotely execute processes.
Check Point attributes this to an unnamed Chinese APT group, which it links to previous operations “dating back to at least 2016—targeting different sectors in multiple countries, such as Ukraine, Russia, and Belarus.” The RTF files were “weaponized” by RoyalRoad, which “is commonly used by Chinese threat actors,” and which exploits “the Equation Editor vulnerabilities of Microsoft Word.”
Forbes interviewed Lotem Finkelsteen, who runs all of Check Point’s research, who told the Forbes reporter:
The remote access trojan launched from within the attachment is coded to limit a daily contact window with its command and control server, making detection more difficult. The architecture of the payload suggests that other modules might be added later as part of the campaign. The trojan “appears to be a custom and unique malware,” albeit the threat specifics are not unusual.
Check Point’s Finkelstein told me the fact “the Chinese group behind this attack, dubbed Vicious Panda, hasn’t been affected by the COVID-19 epidemic is interesting in itself.” Through January and February this year, “the group has released a new cyber weapon, maintained its offensive infrastructure and leveraged the horrific situation to attack foreign countries and companies abroad.”
The irony here? China is using coronavirus to disguise an offensive cyber campaign will not be lost on anyone – it being the root of the infection itself. But the subject matter is currently the most potent social engineering weapon available, and so this latest news comes as no surprise.
Tracking the spread of COVID-19 through mobile phones
This was going to be a separate post, but it’s (somewhat) related so I will stick it here.
As has been widely reported, the U.S. government is in active talks with Facebook, Google and a wide array of tech companies and health experts about how they can use location data gleaned from Americans’ phones to combat novel coronavirus, including tracking whether people are keeping one another at safe distances to stem the outbreak. Public-health experts are interested in the possibility that private-sector companies could compile the data in anonymous, aggregated form, which they could then use to map the spread of the infection.
Analyzing trends in smartphone owners’ whereabouts could prove to be a powerful tool for health authorities looking to track coronavirus, which has now infected 200,000+ globally. But it’s also an approach that could leave some Americans uncomfortable, depending on how it’s implemented, given the sensitivity when it comes to details of their daily whereabouts. Multiple sources stressed that – if they proceed — they are not building a government database.
In recent interviews, Facebook executives said the U.S. government is particularly interested in understanding patterns of people’s movements, which can be derived through data the company collects from users who allow it. The tech giant in the past has provided this information to researchers in the form of statistics, which in the case of coronavirus, could help officials predict the next hotspot or decide where to allocate overstretched health resources.
We all know how this will work out. First China, then Iran, then Israel. This stuff creeps in, always just to help, then won’t get rolled back.