On the heels of my return from a cyber war workshop in Ukraine, even MORE stuff to write about
“Consumers can press ahead with a lawsuit that accuses Apple Inc. of using its market dominance to artificially inflate prices at its App Store, the U.S. Supreme Court ruled. The 5-4 decision Monday could add to pressure the company faces to cut the 30% commission it charges on app sales. Lawyers pressing the case have said they will seek hundreds of millions of dollars on behalf of overpaying consumers.
Apple contended the lawsuit was barred under a 1977 Supreme Court ruling that said only direct purchasers of a product can collect damages for overpricing under federal antitrust law. That decision was designed in part to keep companies from having to pay twice for the same misconduct. Justice Brett Kavanaugh, joining the court’s liberal wing in the majority, said App Store customers meet that test because they buy directly from Apple”
– Bloomburg Business Summary, posted 13 May 2019
14 May 2019 (Berlin, Germany) – Last year I wrote a long client briefing note on this case (Apple vs. Pepper et al, which launched in 2011) for my TMT client base and I indicated the big issue was going to be whether the plaintiffs had standing to sue Apple for antitrust violations at all. In other words, the case hadn’t even started yet. But with this court decision … release the hounds!! Earlier today, several e-discovery vendors launched the discovery process.
The Clayton Antitrust Act of 1914 states that “any person who shall be injured in his business or property by reasons of anything forbidden in the antitrust laws” can bring an antitrust action. BUT … in the 1977 case Illinois Brick Co. v. Illinois, the U.S. Supreme Court held that only direct purchasers of illegally priced goods had standing to sue.
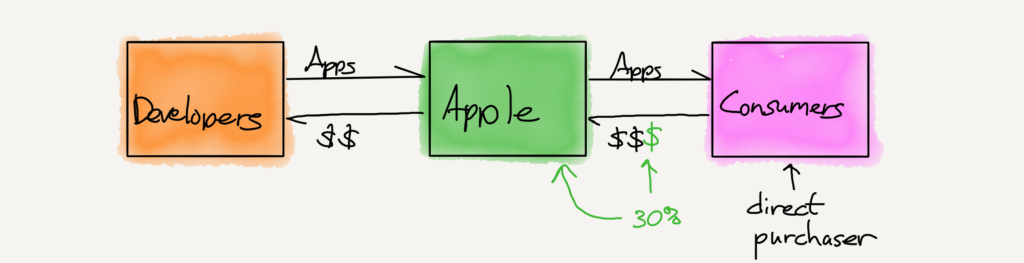
So the question in Apple vs. Pepper, then, is who is directly harmed by Apple’s alleged monopolistic practices. According to the plaintiffs (and borrowing, with permission, two cool sketches from Stratechery done on the fly), the value chain looks like something produced by concrete block manufacturers:
In this case Apple is in between developers and customers. The plaintiffs argue that this makes consumers “direct purchasers”, giving them standing to sue.
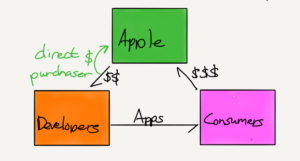
Ah, but Apple argues that the value chain looks like this:
Specifically, the company argues that “Apple does not buy and resell apps” – developers set the price of their apps, which determines Apple’s 30% cut, and to the extent developers set prices higher to compensate for that cut they are passing on alleged harm to consumers. Which means consumers don’t have standing to sue.
To reiterate the key point: the Supreme Court did not determine that the App Store is a monopoly or that Apple has to pay any sort of damages; the majority ruling stated:
At this early pleadings stage of the litigation, we do not assess the merits of the plaintiffs’ antitrust claims against Apple, nor do we consider any other defenses Apple might have. We merely hold that the Illinois Brick direct-purchaser rule does not bar these plaintiffs from suing Apple under the antitrust laws.
The core questions, particularly the most important one — what is the relevant market — remain completely open. The only decision that was made today was answering the question “may we proceed?” You can read the Kavanaugh majority decision, and Justice Gorsuch’s dissent, by clicking here. And ignoring (read: avoiding) the fact that Kavanaugh and Gorsuch are the handmaidens of David Koch and the Federalist Society, both have written considerable opinions as Circuit Judges that have impacted antitrust jurisprudence.
I’m with the dissent on this one
I do think that there are significant antitrust questions around the App Store broadly, and all of FAMGA (Facebook, Apple, Microsoft, Google, Amazon). But I will keep my powder dry for that one, saved for a longer piece I am writing about the futility of the newest “craze”: regulating social media.
In the instant case, the majority argued that Illinois Brick (the details of which I explained in last fall’s client briefing note; if you want it, email me) set out “a bright-line rule” that authorizes suits by direct purchasers but bars suits by indirect purchasers” against alleged antitrust violators. The question in this case, then, is what defines direct versus indirect: is it contractural arrangements and the explicit flow of money, or is it, as the minority argues, “proximate cause and economic reality”? As Ben Thompson, a tech/antitrust blogger, noted:
To be sure, at first glance the majority position seems obvious: customers quite explicitly pay Apple for apps, not developers; any depiction of the app value chain set consumers next to Apple, not developers, even if developers are the ones setting prices.
This, though, is where the minority’s point about economic reality looms large: there is very little to suggest that it is consumers who are bearing the cost of Apple’s 30% as opposed to developers.
I believe that Apple has the stronger position in this case for two reasons: the first are the arguments laid out above. The second, though, comes back to aggregation theory: that Apple has power over developers (supply) precisely because it has all of the consumers (demand); it follows, then, that it is far more likely that developers are pricing according to what the consumer market will bear and internalizing the App Store fee, as opposed to pricing their products artificially high in order to pass the cost of that fee on to customers.
So even if they are pricing their products artificially high that is an ipso facto example of pass-through harm, which means consumers don’t have standing. The plaintiff’s case only makes sense in a world where there is a scarcity of apps with pricing power such that consumers are forced to bear 100% of Apple’s add-on; the reality is that apps are already as cheap as can be and it is developers that are being directly harmed by Apple’s policies.
Look, developers ARE being harmed by Apple’s policies, and those policies are probably illegal. The implication of that, though, is that it is developers who should have the right to sue Apple, not consumers.
And the dissent nails it: the courts will have to divvy up the commissions Apple collected between the developers and the consumers. To do that, they’ll have to figure out which party bore what portion of the overcharge in every purchase. And if the developers bring suit separately from the consumers, Apple might be at risk of duplicative damages awards totaling more than the full amount it collected in commissions.
As both the majority and dissent note, the entire reason behind the Illinois Brick decision was to avoid exactly these sorts of determinations: having one set of damages pursued by two distinct parties is both impractical and overreaching when it comes to judicial power.
It is a mess and this space is small. So let’s move on to WhatsApp …
So WhatsApp, which has touted its high level of security and privacy, with messages on its platform being encrypted end to end so that WhatsApp and third parties cannot read or listen to them, and cannot be hacked … had one doozy of a security flaw. It allowed itself to be exploited so that attackers could inject spyware into victims’ smartphones. And all a snoop needed to do is make a booby-trapped voice call to a target’s number, and they’re in. The victim doesn’t need to do a thing other than leave their phone on.
We’re told that engineers at Facebook scrambled over the weekend to patch the hole, and freshly secured versions of WhatsApp were pushed out to users on Monday. The Facebook website (and several cyber security firms) posted detailed analysis and explanation of the flaw. You can find them at your leisure.
And it’s deja vue all over again. As Ian Thompson noted on The Register:
The Facebook-owned software suffers from a classic buffer overflow weakness. This means a successful hacker can hijack the application to run malicious code that pores over encrypted chats, eavesdrops on calls, turns on the microphone and camera, accesses photos, contacts, and other information on a handheld, and potentially further compromises the device. Call logs can be altered, too, to hide the method of infection.
To pull this off this intrusion, the attacker has to carefully manipulate packets of data sent during the process of starting a voice call with a victim; when these packets are received by the target’s smartphone, an internal buffer within WhatsApp is forced to overflow, overwriting other parts of the app’s memory and leading to the snoop commandeering the chat application.
Exploiting this kind of vulnerability is not trivial. There are highly skilled organizations and companies out there developing tools that can achieve this level of surveillance, tools that are sold to government agencies and other groups to use against specific targets. This exploit would be perfect for a nation’s spies keen to pry into the lives of persons of interest. And as Tom Kennerly of FireEye told me:
After all, why bother cracking WhatsApp’s strong end-to-end encryption when you can overflow a buffer and hack the code itself?
Facebook said the attack had all the hallmarks of a private company known to work with governments to deliver spyware that reportedly takes over the functions of mobile phone operating systems. And they were clearly pointing at the NSO Group which builds exploits and surveillanceware. They sell a highly capable spyware package, dubbed Pegasus, to governments around the world, ostensibly only allowing the suite to be used to snoop on and snare criminals and terrorists. Victims usually get a text message that tries to trick them into following a link that fetches and installs the software nasty.
Now it certainly seems NSO found a way to avoid any user interaction to achieve an automatic, silent infection.
Background: Pegasus, once installed on a victim’s device, can record phone calls, open messages, activate the phone’s camera and microphone for further surveillance, and relay back location data. While NSO claims it carefully vets its customers, the malware has been found on the phones of journalists, human rights campaigners, lawyers, and others.
The subtext is clear: nobody will say outright that this hack was created by NSO/anyone external, but given the expertise needed to find and exploit it is “in the wild”, and it has been happening again and again and again, it is likely that NSO/someone external is at work here. Given that the WhatsApp program is not open source and it has an encryption layer on all its network traffic, I would say that it is at least somewhat hard to find and probably signifies some level of sophistication on the part of the attacker abusing it. This is not “off-the-shelf” cyber attack stuff.
And to use my sandbox analogy (I use it all the time in my cyber posts), once you are in the sandbox you can try to use other techniques. Because you have broad privileges to access other data. And you don’t “install” anything – you just modify the installed app behavior.
Worse, depending on how the app was written, and how much code is shared among other platforms, it’s not difficult for someone with enough resources (and profit) to develop it. Unfortunately, from what I learned about the WhatsApp sandbox, the malware can access contacts, call history, microphone, and camera because of videocalls. That’s enough to compromise the user of the device quite a bit, even if it doesn’t let you read email, browser history, or other types of data on the phone.
And FYI: it was a human rights lawyer who started receiving strange video calls over WhatsApp around three weeks ago in the early hours of the morning and tipped off Citizen Lab, which probes the use of government spyware. The lab then told WhatsApp, which started working on closing the security hole, and learned many lawyers were targeted.