Pour la version française cliquez ici
Für die deutsche Version klicken Sie hier
This is the first in a series of posts covering the Forum which concluded at the end of January 2017
15 February 2017 – It was five and one-half years ago — the fall of 2011 — that I was at the Johns Hopkins University School of Advanced International Studies in Washington, D.C. listening to a keynote address by Joseph Nye at a conference about “Power”.
Nye’s theories on “soft” and “smart” power need no introduction in the field of international relations. No one has done a better job addressing the evolving notion of power in a new world of non-state actors, weak state actors, and emerging economies. His latest book at the time “The Future of Power” had been released earlier that year. As always, meticulously researched, with enormous detail. His manta.
His comments struck a chord and they launched me into a full study of cyber war and cyber security. In his address he noted there were two types of power shifts occurring in this century: power transition and power diffusion. Power transition from one dominant state to another is a familiar historical event, but power diffusion is a more novel process. The problem for all states in today’s global information age is that more things are happening outside the control of even the most powerful states:
“The proliferation of information is as much a cause of non-polarity as is the proliferation of weaponry. We face more and more risks, threats and challenges that affect people in one country but that originate mainly or entirely in the other countries . . . financial crisis, organized crime, mass migration, global warming, pandemics and international terrorism, to name but a few.”
Looking around our world today, one of the main reasons for so much difficulty is that power has been diffused both vertically and horizontally. We have not so much a multi-polar world as a no-polar world. And many observers have noted this trend as marking the decline of the sovereign state that has been the dominant global institutions since the Peace of Westphalia in 1648.
But then Nye’s real payload from that presentation: the Information Revolution — the rapid technological advances in computers, communications, and software that have led to dramatic decreases in the cost of creating, processing and transmitting, and searching for information — will flatten bureaucratic hierarchies and replace them with network organizations. More governmental functions will be handled by private markets as well as by nonprofit entities. A much larger part of the population both within and among countries will have access to the power that comes from information. Governments have always worried about the flow and control of information, and the current period is not the first to be strongly affected by dramatic changes.
And the implicit danger. He believed that the earlier “simple dream” — the rapidity and scope of communication would break down barriers between societies and individuals and provide transparency of such magnitude — was NOT the way it would happen. Just the opposite: cyber networked transparency and the absence of privacy will propel itself into a world without limits or order, forcing us to careen through crises without comprehending them. It’s prime target: the U.S.
Spot on, Mr Nye.
As I have written before, no country has even come close to the U.S. in harnessing the power of computer networks to create and share knowledge, produce economic goods, intermesh private and government computing infrastructure including telecommunications and wireless networks, using all manner of technologies to carry data and multimedia communications, and control all manner of systems for our power energy distribution, transportation, manufacturing, etc. … and so has left the U.S. as the most vulnerable technology ecosystem to those who can steal, corrupt, harm, and destroy public and private assets, at a pace often found unfathomable.
And Europe seems to be approaching a close second.
For most of history, technological change unfolded over decades and centuries of incremental advances that refined and combined existing technologies. Even radical innovations could over time be fitted within previous tactical and strategic doctrines: tanks were considered in terms of precedents drawn from centuries of cavalry; airplanes could be conceptualized as another form of artillery, battleships as mobile forts, and aircraft carriers as airstrips. For all their magnification of destructive power, even nuclear weapons are in some respects an extrapolation from previous experience.
What is new in the present era is the rate of change of computing power and the expansion of information technology into every sphere of existence. Cyberspace — a word coined only in the 198Os — has colonized physical space and, at least in major urban centers, is beginning to merge with it. Communication across it, and between its exponentially proliferating nodes, is near instantaneous. As tasks that were primarily manual or paper based a generation ago — reading, shopping, education, friendship, industrial and scientific research, political campaigns, finance, government record keeping, surveillance, military strategy — are filtered through the computing realm, human activity becomes increasingly “datafied” and part of a single “quantifiable, analyzable” system.
FIC 2017
It is why events such as the International Cybersecurity Forum are so important to attend: to learn about cyber technology, cyber warfare and cyber security; an opportunity to meet the major players in cyber security and take stock of the tendencies and trends regarding cyber attacks, and especially of the solutions now that this problem is becoming so critical and so more general …. as well as becoming a significant economic facet.
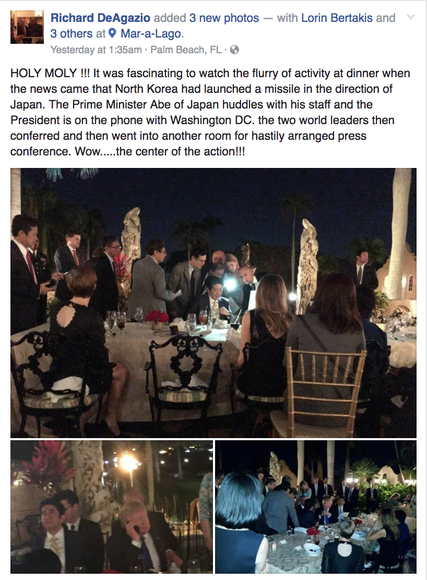
And it is important so you can understand security debacles such as events surrounding the Trump Administration’s “National-Security-As-Theatre”.
White House official response: “Mr. Trump and Mr. Abe had not reviewed classified material on the resort’s patio”.
That’s not the point. As I actually learned at FIC this year, those cellphones-turned-flashlights they were using often have been a problem: if one of them had been hacked by a foreign power, the phone’s camera could have provided a view of what the documents said. And given the intelligence community now knows that Trump’s club is being trolled by electronic surveillance ….
Moreover, the two leaders could have discussed classified documents within earshot of waiters and club patrons. Discussions about how to respond to international incidents involving adversaries like North Korea are almost always conducted in places that have high-tech protections against eavesdropping, like the White House Situation Room. What a great and stupendously simple way for foreign intelligence analysts to gauge the capabilities and effectiveness of a response by the executive power in the land. They’ll be noting the models of phone used, the aides present, the notable absence of military personnel. Maybe there was even a foreign correspondent or foreign national there or two skirting the season. And I wonder who has joined Trump’s exclusive club in the last few weeks. For $200,000 any government can send agents to watch the American president conduct highly classified business in a restaurant. What a deal!
In this series on FIC we will discuss, among other issues:
– the individual digital sphere: what is a connected user to do?
– can awareness-raising be done effectively?
– adopting the cloud: is full security and trust possible?
– automation, AI and the orchestration of incident response
– oh, the productivity war: the daily fight between features and security in the mobile world
– using machine learning for next-generation cyber defense
– How malware like Mirai cannot only hijacked hundreds of thousands of IoT gadgets, routers and other devices but has now been made capable of infecting Windows systems.
– how state-sponsored hackers are attempting to steal email passwords of a number of prominent journalists world-wide, yet another phase of stealing contents of email to be weaponized against their users
– how all of this complexity is compounded by the fact that it is easier to mount cyber attacks than to defend against them, and that has encouraged an offensive bias in the construction of new capabilities
Each part of the series will include a video interview as appropriate with, among others:
- John Frank, Vice President EU Government Affairs for Microsoft
- David Grout, Technical Director for FireEye
- Colonel Nicolas Duvinage, Head of the French National Cybercrime Center
- Oliver Grall, Area Sales Manager of MSAB
- Marcus Klische, Security Advisor to BlackBerry
- Nuvin Goonmeter, Executive Director in Cybersecurity at EY
- Chardy N’Diki, Regional Sales Manager of Centrify
- Frederic Dru, Mobile Sales Specialist at Check Point Software
NOTE: some interviews were conducted in English, and some in French, but each has been subtitled in the opposite language as appropriate.
And for a quick “feeling” of the event …
From the International Cybersecurity Forum in Lille, France: educational sessions, technical demonstrations, solution workshops, start-up pitches, networking cafes, working labs, defensive cyber-warfare competitions, and so much more. Here is a quick look at FIC 2017:
Veteran readers of my blog know my style of writing. The model I try to follow is more like the British magazine tradition of a weekly diary – on the issue, but a little distant from it, personal as well as political, conversational more than formal.
As always, if you have questions or comments please contact us via our Operations Center in Paris at: [email protected]
We hope you enjoy the series.